[ad_1]

For those who obtain an e mail from somebody@arstechnіca.com, is it actually from somebody at Ars? Most undoubtedly not—the area in that e mail deal with isn’t the identical arstechnica.com that you already know. The ‘і’ character in there’s from the Cyrillic script and never the Latin alphabet.
This is not a novel drawback, both. Up till just a few years in the past (however not anymore), fashionable browsers didn’t make any seen distinction when domains containing combined character units had been typed into the deal with bar.
And it seems Microsoft Outlook is not any exception, however the issue simply acquired worse: emails originating from a lookalike area in Outlook would present the contact card of an actual individual, who is definitely registered to the respectable area, not the lookalike deal with.
Outlook exhibits actual contact’s data for spoofed IDN domains
This week, infosec skilled and pentester DobbyWanKenobi demonstrated how they had been in a position to trick the Deal with Ebook part of Microsoft Workplace to show an actual individual’s contact data for a spoofed sender e mail deal with by utilizing IDNs. Internationalized Area Names (IDNs) are domains consisting of a combined Unicode character set, reminiscent of letters from each Latin and Cyrillic alphabets that might make the area seem similar to an everyday ASCII area.
The idea of IDN was proposed in 1996 to increase the area identify house to non-Latin languages and to take care of the aforementioned ambiguity of various characters that look similar (“homoglyphs”) to people. IDNs may simply be represented purely in ASCII format—the “punycode” model of the area, which leaves no room for ambiguity between two lookalike domains.
For instance, copy-pasting the lookalike “arstechnіca.com” into the deal with bar of the newest Chrome browser would instantly flip it into its punycode illustration to stop ambiguity: xn--arstechnca-42i.com. This doesn’t occur when precise arstechnica.com—already in ASCII and with out the Cyrillic ‘і’, is typed into the deal with bar. Such seen distinction is critical to guard the tip customers who might inadvertently land on imposter web sites, used as a part of phishing campaigns.
However not too long ago, DobbyWanKenobi discovered this wasn’t fairly apparent with Microsoft Outlook for Home windows. And the Deal with Ebook characteristic would make no distinction when exhibiting the contact particulars of the individual.
“I not too long ago found a vulnerability that impacts the Deal with Ebook part of Microsoft Workplace for Home windows that might permit anybody on the web to spoof contact particulars of workers inside a corporation utilizing an exterior look-alike Internationalized Area Title (IDN),” wrote the pentester in a weblog publish. “This implies if an organization’s area is ‘somecompany[.]com’, an attacker that registers an IDN reminiscent of ‘ѕomecompany[.]com’ (xn--omecompany-l2i[.]com) may benefit from this bug and ship convincing phishing emails to workers inside ‘somecompany.com’ that used Microsoft Outlook for Home windows.”
Coincidentally, the next day, one other report on the subject emerged from Mike Manzotti, a senior marketing consultant at Dionach. For a contact created on Manzotti’s “onmìcrosoft.com” area (discover the ì), Outlook displayed legitimate contact particulars of the individual whose e mail deal with contained the true “onmicrosoft.com” area.
“In different phrases, the phishing e mail targets the person NestorW@….onmìcrosoft.com, nonetheless, legitimate Energetic Listing particulars and picture of NestorW@….onmicrosoft.com are displayed as if the e-mail was coming from a trusted supply,” says Manzotti.
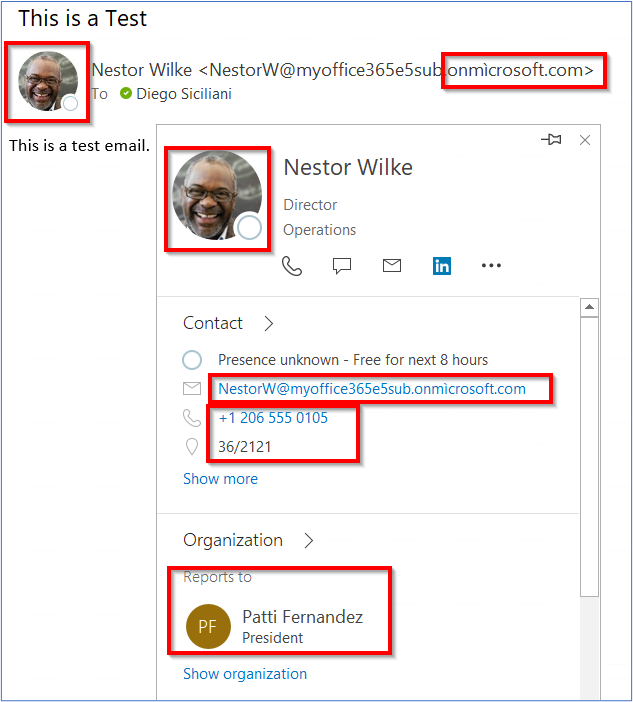
Manzotti has traced the reason for the difficulty to Outlook not accurately validating e mail addresses in Multipurpose Web Mail Extensions (MIME) headers.
“While you ship an HTML e mail you may specify the SMTP ‘mail from’ deal with, and the Mime ‘from’ deal with,” explains Manzotti.
“It is because the MIME headers are encapsulated into the SMTP protocol. MIME is used for extending easy textual content messages, for instance when sending HTML emails,” he defined with an illustration:
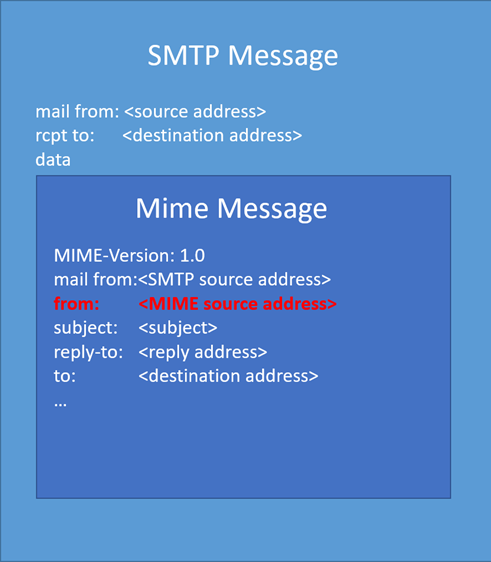
However, in accordance with Manzotti, Microsoft Outlook for Workplace 365 doesn’t accurately confirm the punycode area, letting an attacker impersonate any legitimate contact within the goal group.
IDN phishing: An previous drawback revived
The issue of IDN-based phishing web sites gained the highlight in 2017 when net utility developer Xudong Zheng demonstrated how fashionable browsers, on the time, failed to differentiate his аpple.com look-alike web site (an IDN) from the true apple.com.
Zheng was involved that IDNs could possibly be abused by attackers for varied nefarious functions reminiscent of phishing:
From a safety perspective, Unicode domains might be problematic as a result of many Unicode characters are tough to differentiate from widespread ASCII characters. It’s doable to register domains reminiscent of “xn--pple-43d.com”, which is equal to “аpple.com”. It will not be apparent at first look, however “аpple.com” makes use of the Cyrillic “а” (U+0430) reasonably than the ASCII “a” (U+0061). This is named a homograph assault.
However the issue in Outlook is that for a phishing e mail despatched from an IDN, the recipient might not solely fail to differentiate between the spoofed e mail deal with and the true one but additionally see the contact card of a respectable contact, due to this fact falling sufferer to the assault.
It’s unclear if Microsoft is inclined to repair the difficulty in Outlook at the moment:
“We have completed going over your case, however on this occasion, it was determined that we’ll not be fixing this vulnerability within the present model,” a Microsoft employees member is seen telling DobbyWanKenobi in an e mail.
“Whereas spoofing may happen, the sender’s id can’t be trusted and not using a digital signature. The modifications wanted are prone to trigger false positives and points in different methods,” continued the e-mail seen by Ars:
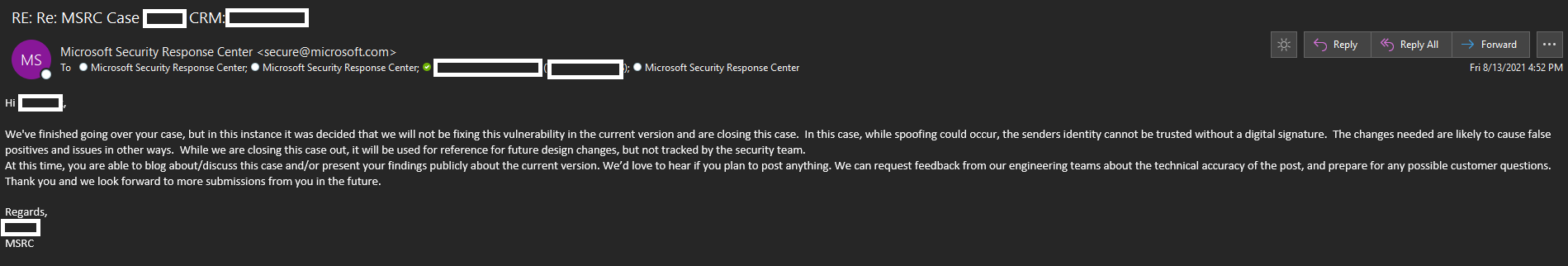
Microsoft has not responded to Ars’ request for remark despatched out upfront.
Researchers have seen this vulnerability impacting each 32-bit and 64-bit variations of the newest Microsoft Outlook for Microsoft 365 variations, though it seems the difficulty was not reproducible on model 16.0.14228.20216 after Manzotti notified Microsoft.
Oddly sufficient, Microsoft’s response to Manzotti maintained that the vulnerability is not going to be fastened. Moreover, Manzotti notes such a phishing assault will not succeed on Outlook Internet Entry (OWA).
Profiting from security measures reminiscent of “exterior sender” e mail warnings and e mail signing are just a few steps organizations can take to discourage spoofing assaults.
Supply arstechnica.com
