
Enlarge / On this story, we’ll find out about “pig butchering.”
Aurich Lawson / Getty Pictures
There are, by some estimates, extra good telephones on this planet than human beings to make use of them. Individuals who have by no means used a desktop pc use good telephones and different cell units day by day and have a lot of their lives tethered to them—possibly greater than they need to.
Because of this, cyber-grifters have shifted their focus from sending emails to gullible private pc customers (pretending to be Nigerian princes in want of banking help) and have as a substitute set their sights on the better goal of mobile phone customers. Criminals are utilizing smartphone apps and textual content messages to lure weak individuals into traps—some with purely monetary penalties, and a few that put the victims in precise bodily jeopardy.
I just lately outlined some methods to use a little bit of armor to our digital lives, however latest traits in on-line scams have underscored simply how simply smartphones and their apps may be turned in opposition to their customers. It is price reviewing these worst-case situations to assist others spot and keep away from them—and we aren’t simply speaking about serving to older customers with this. These items impacts everybody.

Enlarge / Uh oh, Hoodie McHackerman is again, and now he is after your telephones.
PeopleImages / Getty Pictures
I’ve personally been contacted by quite a lot of individuals who’ve been victims of mobile-focused scams and by individuals who’ve discovered themselves uncovered and focused through sudden vulnerabilities created by interactions with cell apps. For some, these experiences have shattered their sense of privateness and safety, and for others, these scams have price them hundreds (or tens of hundreds) of {dollars}. In mild of this, it is price arming your self and your loved ones with info and an entire lot of skepticism.
Focused SMS phishing
The final two years have seen an amazing uptick in textual content message phishing scams that concentrate on private knowledge—particularly web site credentials and bank card knowledge. Generally known as “smishing,” SMS phishing messages normally carry some name to motion that motivates the recipient to click on on a hyperlink—a hyperlink that always results in an online web page that’s supposed to steal usernames and passwords (or do one thing worse). These spam textual content messages are nothing new, however they’re changing into more and more extra focused.
In 2020, the FTC reported that US shoppers misplaced $86 million because of rip-off texts, and the FCC went so far as to situation a warning about COVID-19 textual content scams. Positive, certain, you are good and you’d by no means quit your private knowledge to a sketchy textual content message. However what if the textual content talked about your identify, together with sufficient appropriate info to make you simply the slightest bit involved? Like a textual content message purportedly out of your financial institution, giving your identify, asking you to log in to verify or contest a $500 cost in your bank card at Walmart?

Enlarge / Cell scams are in all places, however they normally aren’t being perpetrated by scary dudes in hoodies, inventory artwork however.
BrianAJackson / Getty Pictures
That is the sort of message I just lately obtained. If I had not learn the message rigorously or seen that it had come from a spoofed cellphone quantity that was not linked to my financial institution or did not keep in mind that I had by no means consented to any communications with my financial institution through textual content messages, I might need clicked.
As a substitute, I went into my financial institution’s cell app and located a discover on the login web page that prospects had been experiencing fraud makes an attempt via textual content messages. I took the hyperlink to my pc and pulled down the web page utilizing wget. The hyperlink pointed at a Google App Engine web page that contained a hyperlink in an IFRAME factor to a Russian web site—one which tried to emulate the financial institution’s web site login.
SMS scams like these are made simpler by the rafts of public knowledge publicity and the aggregation of non-public particulars by entrepreneurs. This type of knowledge is all too usually collected in databases that get leaked or hacked. Scammers can goal giant numbers of consumers of a particular model simply by connecting their relationship to an organization with their cellphone numbers. I haven’t got good scientific knowledge on the prevalence of focused “smishing,” however a random sampling of household and mates signifies it isn’t only a passing drawback: in some instances it constitutes half of the day by day SMS messages they obtain.
Most of it’s the equal of pop-up net adverts. Among the focused SMS messages I’ve seen have presupposed to be from frequent providers—like Netflix, for instance:
Netflix: [Name], please replace your membership with us to proceed watching. [very sketchy URL]
The sketchy hyperlink led to a website claiming my final cost had been declined, and I had 48 hours to re-activate my account.
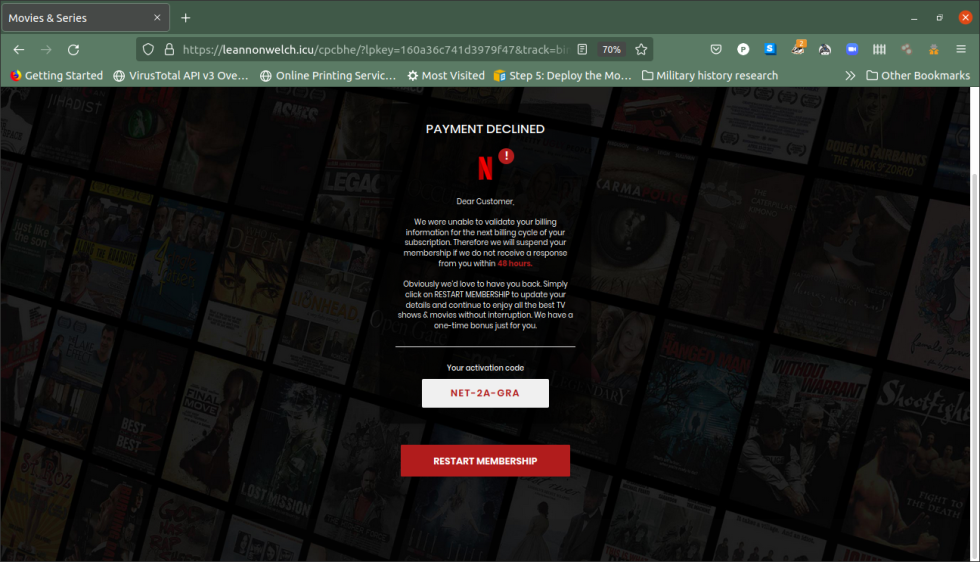
Enlarge / A really sketchy website certainly.
Clicking on that hyperlink funnels you right into a collection of web page forwards powered by a “tracker” website configured to filter out suspicious clicks (like ones from PC browsers), sending solely cell browsers to the supposed vacation spot—on this case, a Netflix look-alike service that tries to get you to enroll as a member. Your IP deal with is without doubt one of the arguments handed to the ultimate URL in an effort to hold out undesirable ranges of “prospects.”
That is mild scamming, to make sure. However the identical tracker websites are utilized by a variety of scams, together with SMS and cell browser pop-up “faux alert” scams. A majority of these scams usually function an pressing name to motion. One other frequent angle is claiming that the recipient’s IP deal with “is being tracked as a result of viruses,” with a hyperlink that results in an app retailer web page—normally some sort of questionable digital personal community app that will actually do nothing aside from accumulate “in-app funds” via the Apple or Google app shops for a service that does not work. Or the service does work—however not in ways in which the gadget proprietor would love.
Fleece apps and pretend apps
Regardless of efforts by huge corporations to examine the safety of purposes earlier than they’re supplied for obtain on app shops, scammer builders commonly handle to slide nasty issues into the iOS and Android marketplaces—nasty low-cost or “free” apps of restricted (or nonexistent) usefulness that deceive customers into paying giant quantities of cash.

Enlarge / Set up this app, OR ELSE.
Chanin Wardkhian / Getty Pictures
Typically, these purposes are offered as free however function in-app funds—together with subscription charges that routinely kick in after a really quick “trial interval” that will not be absolutely clear to the consumer. Sometimes called “fleeceware,” apps like this may cost regardless of the developer needs on a repeating foundation. And so they might even proceed to generate fees after a consumer has uninstalled the appliance.
To make certain that you are not being charged for apps you’ve got eliminated, it’s important to go examine your record of subscriptions (this works in another way on iOS and Google Play)—and take away any that you just aren’t utilizing.
Sometimes, malicious purposes handle to slide previous app retailer screening. When caught, the developer accounts related to the apps are normally suspended—and the apps are faraway from the shops and (normally) from units they have been put in on. However the builders of those apps usually simply roll over to a different developer account or use different methods to get their apps in entrance of customers.
I tracked a marketing campaign of pop-up adverts that drove good cellphone customers to “safety” purposes on each app shops, utilizing faux alert pages resembling cell working system alerts that warned of virus infections on units. When the adverts detected an iOS gadget, they ended by opening the web page of a VPN software from a developer in Belarus that charged $10 per week for service. The app retailer itemizing was replete with (probably faux) 4-star evaluations, together with just a few from precise prospects who found that they had been scammed.
The app itself labored, kind of—it directed all customers’ Web visitors via a server in Belarus, permitting for man-in-the-middle assaults and the gathering of huge quantities of consumer knowledge.
Positive, a classy gadget consumer would know that these apps are fraudulent and spot them instantly, proper? Presumably—however what number of iOS and Android customers have that stage of sophistication?

