GOT ROOT —
It’s seemingly best a subject of time sooner than PwnKit is exploited inside the wild.
Dan Goodin –

Linux prospects on Tuesday purchased a essential dose of sinful data—a 12-yr-extinct vulnerability in a intention machine often known as Polkit presents attackers unfettered root privileges on machines working most main distributions of the initiating present working intention.
Beforehand often known as PolicyKit, Polkit manages intention-broad privileges in Unix-esteem OSes. It presents a mechanism for nonprivileged processes to soundly maintain interplay with privileged processes. It furthermore permits prospects to interrupt directions with extreme privileges by using a ingredient often known as pkexec, adopted by the clarify.
Trivial to revenue from and 100 p.c suited
Esteem most OSes, Linux presents a hierarchy of permission phases that controls when and what apps or prospects can maintain interplay with delicate intention sources. The injury is meant to limit the shatter that may occur if a selected individual isn’t relied on to carry administrative maintain a watch on of a community or if the app is hacked or malicious.
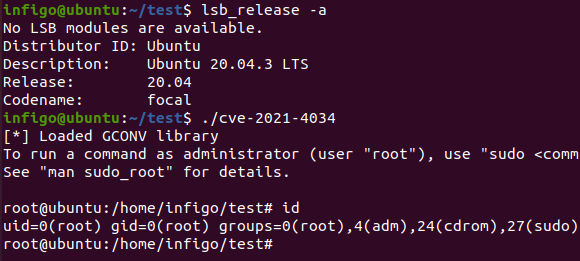
Since 2009, pkexec has contained a reminiscence-corruption vulnerability that people with restricted maintain a watch on of a inclined machine can exploit to escalate privileges all how chances are you’ll per probability properly presumably furthermore root. Exploiting the flaw is trivial and, by some accounts, 100 p.c suited. Attackers who already maintain a toehold on a inclined machine can abuse the vulnerability to understand apparent {that a} malicious payload or clarify runs with the highest intention rights available. PwnKit, as researchers are calling the vulnerability, is furthermore exploitable even though the Polkit daemon itself isn’t working.
PwnKit was once came across by researchers from safety firm Qualys in November and was once disclosed on Tuesday after being patched in most Linux distributions. PwnKit is tracked as CVE-2021-4034.
In an e mail, Qualys Director of Vulnerability Threat Study Bharat Jogi wrote:
The presumably assault situation is from an inside probability the place a malicious specific individual can escalate from no privileges by any potential to paunchy root privileges. From an exterior probability standpoint, if an attacker has been prepared to understand foothold on a intention by one different vulnerability or a password breach, that attacker can then escalate to paunchy root privileges by this vulnerability.
Jogi acknowledged exploits require native authenticated obtain entry to to the inclined machine and might properly properly furthermore’t be stride remotely with out such authentication. Right here’s a video of the exploit in motion.
PwnKit Vulnerability.
For now, Qualys isn’t releasing proof-of-thought exploit code out of area the code will cloak extra of a boon to shadowy hats than to defenders. PoC code has been launched by one different present, and researchers acknowledged that it’s best a subject of time till PwnKit is exploited inside the wild.
“We search data from that the exploit will flip into public quickly and that attackers will originate exploiting it—that is significantly horrible for any multi-particular individual intention that permits shell obtain entry to to prospects,” Bojan Zdrnja, a penetration tester and a handler at SANS, wrote. The researcher acknowledged he efficiently recreated an exploit that labored on a machine working Ubuntu 20.04.
The Qualys researchers are not mainly the best ones to come across this vulnerability, or not not as much as a really an identical computer virus. In 2013, researcher Ryan Mallon publicly reported a lot the an identical computer virus and even wrote a patch, although he eventually might properly properly presumably get no approach to revenue from the vulnerability. And shutting June, Github safety researcher Kevin Backhouse furthermore reported a privilege escalation vulnerability. It obtained the monitoring designation of CVE-2021-3560 and a patch from main Linux distributors.
Lol, I blogged about this polkit vulnerability in 2013: https://t.co/a6ciqwCmyt. I did not search out an correct avenue for exploitation, nonetheless did title the inspiration motive.
— Ryan Mallon (@ryiron) January 26, 2022
SANS
Predominant Linux distributors maintain launched patches for the vulnerability, and safety specialists are strongly urging directors to prioritize putting in the patch. Those that can’t patch abruptly should simple use the chmod 0755 /usr/bin/pkexec clarify to understand the SUID-bit from pkexec, which prevents it from working as root when finished by a non-privileged specific individual. Advisories from Debian, Ubuntu, and Crimson Hat are proper right here, proper right here, and proper right here.
Those that maintain to know if the vulnerability has been exploited on their applications can check out for log entries that dispute each “The value for the SHELL variable was once not came across the /and heaps others/shells file” or “The value for environment variable […] comprises suspicious philosophize materials.” Qualys, then as quickly as extra, cautioned people that PwnKit is furthermore exploitable with out leaving any traces.

