
Getty Images
Over the previous couple of months, geopolitical tensions possess escalated as Russia amassed tens of tons of of troops alongside Ukraine’s border and made refined however a ways-reaching threats if Ukraine and NATO don’t conform to Kremlin requires.
Now, a identical dispute is collaborating in out in cyber arenas, as unknown hackers gradual last week defaced rankings of Ukrainian authorities internet sites and left a cryptic warning to Ukrainian voters who tried to collect companies.
Be frightened and quiz the worst
“All recordsdata on the laptop computer is being destroyed, it’s inconceivable to reinforce it,” talked about a message, written in Ukrainian, Russian, and Polish, that appeared gradual last week on now not now not as quite a bit as a couple of the contaminated techniques. “All information about you has turned public, be frightened and quiz the worst.”
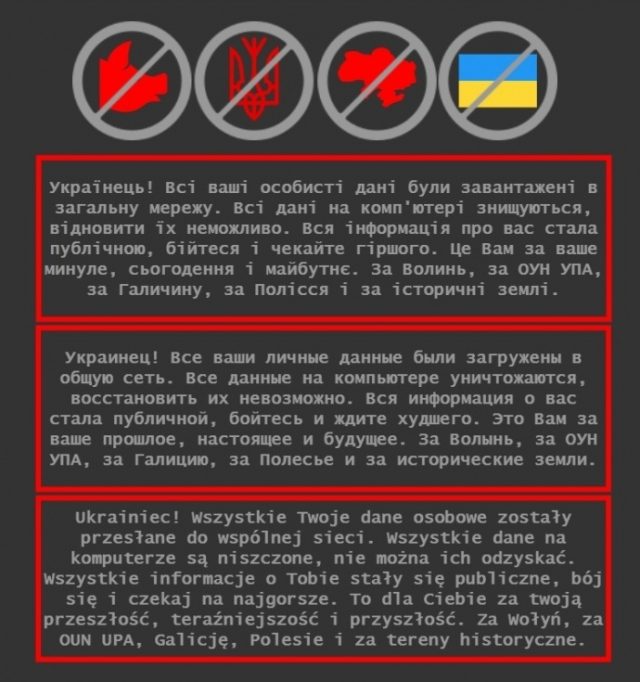
Across the the identical time, Microsoft wrote in a publish over the weekend, “harmful” malware with the potential to completely murder laptop computer techniques and all recordsdata saved on them began displaying on the networks at dozens of authorities, nonprofit, and knowledge expertise organizations, all basically based mostly in Ukraine. The malware—which Microsoft is asking Whispergate—masquerades as ransomware and requires $10,000 in bitcoin for recordsdata to be restored.
Nonetheless Whispergate lacks the plan by which to distribute decryption keys and current technical improve to victims, traits which can be chanced on in practically about all working ransomware deployed within the wild. It additionally overwrites the grasp boot file—a facet of the exhausting stress that begins the working blueprint for the duration of bootup.
“Overwriting the MBR is odd for cybercriminal ransomware,” members of the Microsoft Risk Intelligence Center wrote in Saturday’s publish. “Absolutely, the ransomware mumble is a ruse and that the malware destructs MBR and the contents of the recordsdata it targets. There are a number of the rationalization why this job is inconsistent with cybercriminal ransomware job noticed by MSTIC.”
Over the weekend, Serhiy Demedyuk, deputy head of Ukraine’s Nationwide Safety and Protection Council, advised information retailers that preliminary findings from a joint investigation of a number of Ukrainian enlighten companies current {that a} risk actor neighborhood recognized as UNC1151 was once probably gradual the defacement hack. The neighborhood, which researchers at security agency Mandiant possess linked to the authorities of Russian ally Belarus, was once gradual an influence advertising and advertising and advertising marketing campaign named Ghostwriter.
Ghostwriter labored by way of phishing emails and theft domains that spoof plentiful internet sites quite a bit like Fb to blueprint shut sufferer credentials. With tackle watch over of affirm materials administration techniques belonging to information websites and diversified closely trafficked properties, UNC1151 “basically promoted anti-NATO narratives that appeared imagined to undercut regional security cooperation in operations concentrating on Lithuania, Latvia, and Poland,” authors of the Mandiant chronicle wrote.
All proof solutions to Russia
Ukrainian officers talked about UNC1151 was once probably engaged on behalf of Russia when it broken-down its potential in harvesting credentials and infiltrating internet sites to deface Ukraine’s authorities websites. In a commentary, they wrote:
As of now, we are able to mutter that each individual the proof solutions to the reality that Russia is gradual the cyber assault. Moscow continues to wage a hybrid warfare and is actively establishing forces within the knowledge and our on-line world.
Russia’s cyber-troops are assuredly working in opposition to the usa and Ukraine, trying to utilize expertise to shake up the political enterprise. Probably the most smooth cyber assault is a few of the manifestations of Russia’s hybrid warfare in opposition to Ukraine, which has been occurring since 2014.
Its simply is now not most efficient to intimidate society. And to destabilize the enterprise in Ukraine by stopping the work of the general public sector and undermining the confidence within the authorities on the fragment of Ukrainians. They will enact this by throwing fakes into the infospace concerning the vulnerability of principal recordsdata infrastructure and the “drain” of personal recordsdata of Ukrainians.
Injure evaluation
There have been no instantaneous experiences of the defacements having a harmful halt on authorities networks, although Reuters on Monday reported Ukraine’s cyber police chanced on that last week’s defacement appeared to own destroyed “exterior recordsdata sources.”
“A desire of exterior recordsdata sources had been manually destroyed by the attackers,” the police talked about, with out elaborating. The police added: “It’s going to already be argued that the assault is further complicated than modifying the homepage of websites.”
Microsoft, in the meantime, didn’t mutter if the dangerous recordsdata wiper it chanced on on Ukrainian networks had merely been put in for potential use later or if it had little doubt been executed to wreak havoc.
There’s no proof that the Russian authorities had any involvement within the wiper malware or the net net affirm defacement, and Russian officers possess flatly denied it. Nonetheless given earlier events, Russian involvement wouldn’t be a shock.
In 2017, an unlimited outbreak of malware on the beginning up believed to be ransomware shut down laptop computer techniques everywhere in the realm and resulted in $10 billion in whole damages, making it the most costly cyberattack ever.
NotPetya on the beginning up unfold by way of a plentiful replace module of M.E.Doc, a tax-accounting software program that’s broadly broken-down in Ukraine. Each Ukrainian and US authorities officers possess talked about Russia was once gradual the assaults. In 2020, federal prosecutors charged 4 Russian nationals for alleged hacking crimes animated NotPetya.

