PUTTING CSRF ON NOTICE —
Hackers discover prolonged passe browsers as a beachhead. Google targets for PNA to change that.
Dan Goodin –

For greater than a decade, the Information superhighway has remained at probability of a class of assaults that makes use of browsers as a beachhead for gaining access to routers and different trustworthy units on a targeted community. Now, Google is lastly doing one factor about it.
Starting in Chrome model 98, the browser will delivery up relaying requests when public web sites want to discover admission to endpoints inside the non-public community of the person visiting the space. In the interim, requests that fail may not dwell the connections from occurring. As another, they’re going to easiest be logged. Someplace spherical Chrome 101—assuming the implications of this trial depart do not mark elementary elements of the Information superhighway shall be broken—it will be important for public web sites to seek out specific permission ahead of they will discover admission to endpoints behind the browser.
The deliberate deprecation of this discover admission to comes as Google permits a current specification recognized as private community discover admission to, which allows public web sites to seek out admission to inside community sources easiest after the web sites discover explicitly requested it and the browser grants the put a query to. PNA communications are despatched the make use of of the CORS, or Horrifying-Starting Useful resource Sharing, protocol. Underneath the plan, the ultimate public house sends a preflight put a query to inside the invent of the current header Entry-Administration-Ask-Private-Community: factual. For the put a query to to be granted, the browser should acknowledge with the corresponding header Entry-Administration-Permit-Private-Community: factual.
Community intrusion by the use of the browser
So far, web sites discover by default had the flexibility to make make use of of Chrome and different browsers as a proxy for gaining access to sources inside the native community of the person visiting the space. Whereas routers, printers, or different community sources are on the ultimate locked down, browsers—as a consequence of the necessity for them to seek out interplay with so many companies and merchandise—are by default accredited to attach with merely about any helpful useful resource inside the native community perimeter. This has given rise to a class of assault recognized as a CSRF, speedy for imperfect-space put a query to forgery.
Such assaults had been theorized for greater than a decade and discover additionally been carried out inside the wild, on the ultimate with important penalties. In a single 2014 incident, hackers passe CSRFs to change the DNS server settings for greater than 300,000 wi-fi routers.
The change introduced on the compromised routers to make make use of of malicious DNS servers to seek out to the underside of the IP addresses stop prospects had been making an attempt to hunt the advice of with. As another of visiting the dependable Google.com house, as an illustration, the malicious server may return the IP handle for a boobytrapped imposter house that the tip person has no purpose to think about is wicked. The picture under, from researchers at Crew Cymru, reveals the three steps involved about these assaults.
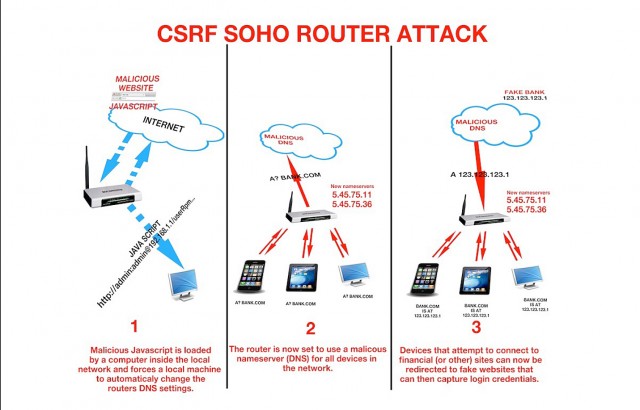
Develop / Three phases of an assault that modifications a router’s DNS settings by exploiting a imperfect-space put a query to vulnerability inside the instrument’s Internet interface.
Crew Cymru
In 2016, people behind the similar assault returned to push malware recognized as DNSChanger. As I outlined on the time, the selling and advertising and marketing marketing campaign labored in opposition to residence and dwelling of enterprise routers made by Netgear, DLink, Comtrend, and Pirelli this type:
DNSChanger makes use of a impact of precise-time communications protocols recognized as webRTC to ship so-known as STUN server requests passe in VoIP communications. The exploit is one map or the other able to funnel code by the use of the Chrome browser for Dwelling home windows and Android to prevail inside the community router. The assault then compares the accessed router in opposition to 166 fingerprints of recognized inclined router firmware images.
Assuming the PNA specification goes totally into perform, Chrome will not permit such connections besides units inside the non-public community explicitly permit it. Listed under are two diagrams displaying the way it undoubtedly works.
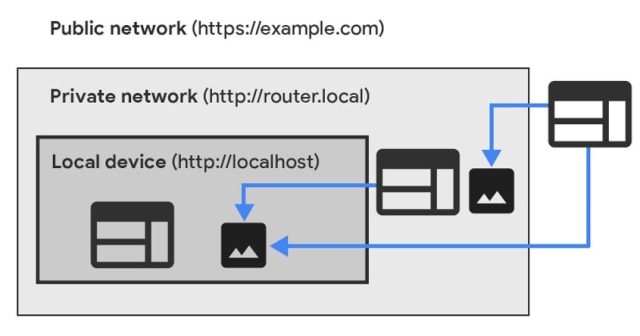
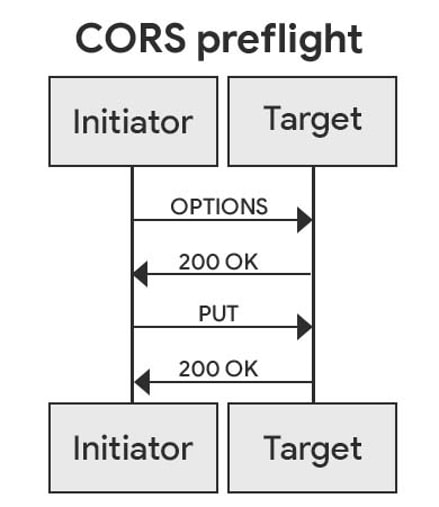
The avenue ahead
Starting in model 98, if Chrome detects a private community put a query to, a “preflight put a query to” shall be despatched ahead of time. If the preflight put a query to fails, the closing put a query to will unexcited be despatched, however a warning shall be surfaced inside the DevTools considerations panel.
“Any failed preflight put a query to will stop in a failed procure,” Google engineer Titouan Rigoudy and Google developer Eiji Kitamura wrote in a most neatly-liked weblog submit. “This would possibly perhaps nicely perhaps nicely imply chances are you will perhaps nicely perhaps perhaps check out whether or not your net house would work after the second section of our rollout perception. Errors can also be recognized inside the similar map as warnings the make use of of the DevTools panels talked about above.”
If and when Google is assured there is not going to be any longer going to be mass disruptions, preflight requests will want to be granted to try in opposition to by the use of.

