DECEPTION —
Factual in the event you occur to perception you have to be succesful to thought of each phishing trick out there, BitB comes alongside.
Dan Goodin –

Getty Pictures
As soon as we inform individuals the way you probably may protect a methods from falling sufferer to phishing web websites, we in whole yelp fastidiously inspecting the care for bar to make sure that it does have HTTPS and that it doesn’t have suspicious domains equal to google.evildomain.com or change letters equal to g00gle.com. However what if somebody came upon a method to phish passwords the utilization of a malicious set up that didn’t have these telltale indicators?
One researcher has devised a method to hold out merely that. He calls it a BitB, quick for “browser within the browser.” It makes use of a defective browser window inside a precise browser window to spoof an OAuth web page. Lots of of 1000’s of web websites expend the OAuth protocol to let firm login the utilization of their distinctive accounts with corporations esteem Google, Fb, or Apple. As an change of attending to assemble an account on the modern set up, firm can expend an account that they have already got—and the magic of OAuth does the consolation.
Exploiting trust
The picture modifying set up Canva, as an illustration, provides firm the chance to login the utilization of any of three frequent accounts. The photographs beneath yelp what a selected individual sees after clicking the “register” button; following that, the picture yelp what appears after choosing to register with a Google password. After the precise individual chooses Google, a model modern browser window with a sound care for opens in entrance of the distinctive Canva window.
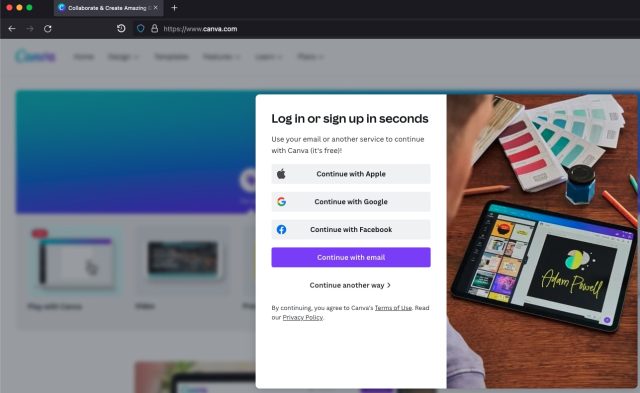
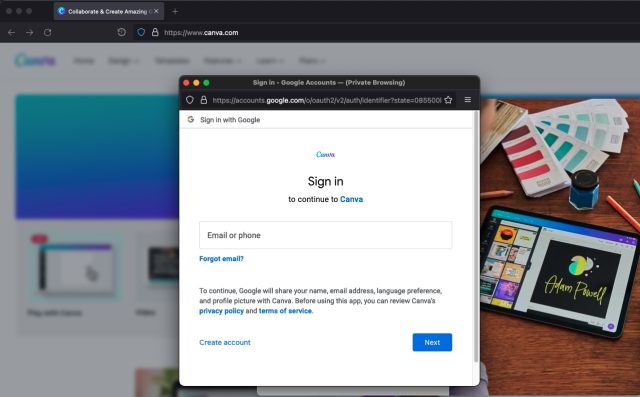
The OAuth protocol ensures that most interesting Google receives the precise individual password. Canva by no methodology sees the credentials. As an change, OAuth securely establishes a login session with Google and, when the username and password take a look at out, Google provides the customer with a token that gives bag entry to to Canva. (One factor equal occurs when a consumer chooses a value system esteem PayPal.)
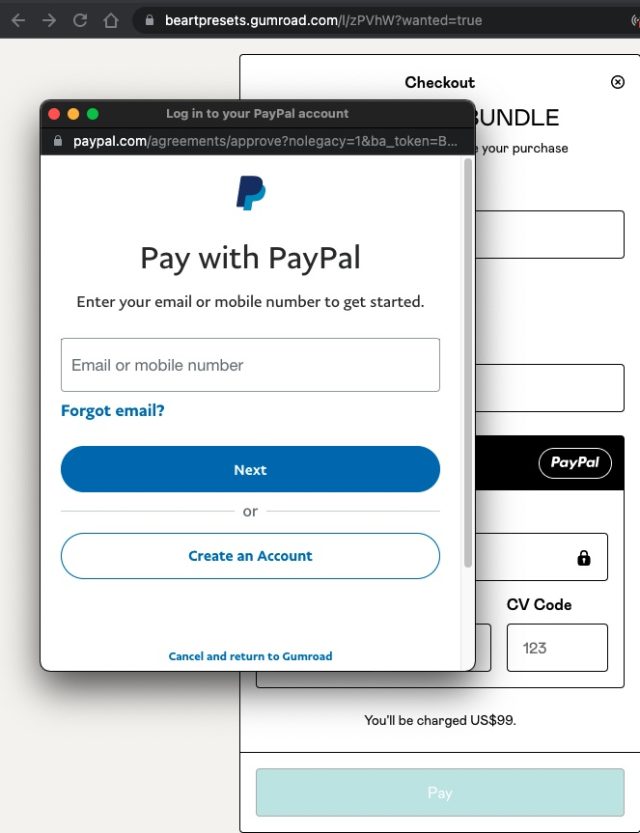
The BitB approach capitalizes on this scheme. As an change of opening a protected 2nd browser window that’s related to the set up facilitating the login or value, BitB makes use of a sequence of HTML and cascading sort sheets (CSS) tips to convincingly spoof the 2nd window. The URL that appears there can yelp a kindly care for, complete with a padlock and HTTPS prefix. The format and habits of the window appear equal to the exact part.
A researcher the utilization of the shape out mr.d0x described the approach final week. His proof-of-concept exploit begins with a Internet web page on-line exhibiting a painstakingly most interesting spoofing of Canva. Inside the event a customer chooses to login the utilization of Apple, Google, or Fb, the defective Canva web page opens a model modern web page that embeds what seems esteem the familiar-attempting OAuth web page.

This modern web page is furthermore a spoof. It entails the entire graphics a selected individual would request to leer when the utilization of Google to login. The web page furthermore has the legit Google care for displayed in what seems the care for bar. The modern window behaves noteworthy esteem a browser window would if related to a precise Google OAuth session.
If a probably sufferer opens the defective Canva.com web page and tries to login with Google, “this might even originate a model modern browser window and scamper to [what appears to be] the URL accounts.google.com,” mr.d0x wrote in a message. Absolutely, the defective Canva set up “doesn’t originate a model modern browser window. It makes it LOOK esteem a model modern browser window was as quickly as opened but it surely undoubtedly’s most interesting HTML/CSS. Now that defective window units the URL to accounts.google.com, however that’s an illusion.”
Malvertisers: please originate no longer learn this
A fellow security researcher was as quickly as impressed satisfactory by the demonstration to assemble a YouTube video that extra vividly reveals what the approach seems esteem. It furthermore explains how the approach works and the way simple it’s to give up.
Browser within the Browser (BITB) Phishing Methodology – Created by mr.d0x
The BitB approach is simple and wonderful satisfactory that it’s most interesting it isn’t higher recognized. After mr.d0x wrote in regards to the approach, a shrimp refrain of fellow researchers remarked how probably it would be for much more expert Web customers to tumble for the trick. (mr.d0x has made proof of idea templates readily available right here.)
“This browser-in-the-browser assault is very most interesting for phishing,” one developer wrote. “Concurrently you shall be centered on malvertising, please originate no longer learn this. We originate no longer must current you with suggestions.”
“Ooh that’s unsuitable: Browser In The Browser (BITB) Assault, a model modern phishing approach that allows stealing credentials that even a web expert can’t detect,” one different specific individual acknowledged.
The approach has been actively well-liked within the wild no longer decrease than as quickly as earlier than. As security firm Zscaler reported in 2020, scammers well-liked a BitB assault in an attempt to protect credentials for on-line sport distribution provider Steam.
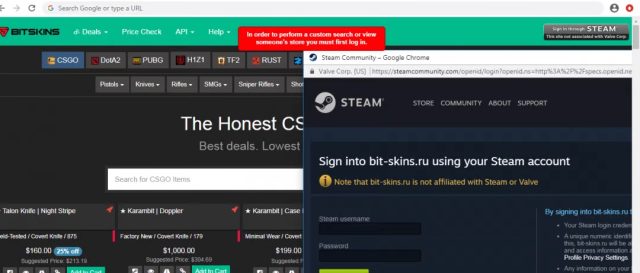
Whereas the system is convincing, it has a few weaknesses that should current savvy firm a foolproof methodology to detect that one thing is amiss. Devoted OAuth or value home windows are actually separate browser circumstances which might be sure from the precept web page. Which means a selected individual can resize them and cross them anyplace on the present display screen, together with outside the precept window.
BitB home windows, in distinction, aren’t a separate browser occasion in the slightest degree. As an change, they’re photographs rendered by customized HTML and CSS and contained within the precept window. Which means the defective pages can’t be resized, absolutely maximized or dragged outside the precept window.
Sadly, as mr.d0x recognized, these assessments might be irritating to teach “on account of now we cross a methods from the ‘take a look at the URL’” recommendation that’s long-established. “You’re instructing customers to hold out one thing they by no methodology perform.”
All customers should defend their accounts with two-component authentication. One fairly a few part extra expert customers can perform is acceptable click on on the popup web page and protect terminate “ogle.” If the window is a BitB spawn, its URL might be hardcoded into the HTML.
It wouldn’t be most interesting to go looking out that the BitB approach has been extra broadly well-liked, however the response mr.d0x purchased demonstrates that many security defenders should not aware of BitB. And which methodology loads of keep customers aren’t, both.

