LIFE AND TIMES OF CONTI —
Practically two years value of chat logs air the neighborhood’s soiled laundry.
Dan Goodin –

For months, members of Conti—among the many many most ruthless of the handfuls of ransomware gangs in existence—gloated about publicly sharing the rules they stole from the victims they hacked. Now, members are finding out what it’s cherish to be on the receiving conclude of a major breach that spills all their soiled laundry—not simply actual as quickly as, nonetheless many situations.
The unfolding sequence of leaks began on Sunday when @ContiLeaks, a newly created Twitter yarn, began posting hyperlinks to logs of interior chat messages that Conti members had despatched amongst themselves.
Two days later, ContiLeaks revealed a model up to date tranche of messages.
Burn it to the ground
On Wednesday, ContiLeaks was once abet with extra leaked chats. Probably the most modern dispatch confirmed headers with dates from Tuesday and Wednesday, a sign that the unknown leaker persevered to beget acquire entry to to the staff’s interior Articulate/XMPP server.
“Howdy, how are points with us?” a Conti worker referred to as Tort wrote in a Wednesday message to a gang colleague named Inexperienced, in accordance with Google Translate. Tort went on to file that any particular person had “deleted the overall farms with a shredder and cleaned the servers.” This type of change prompt that Conti was once dismantling its worthy infrastructure out of terror the leaks would say members to legislation enforcement investigators all of the contrivance by the enviornment.
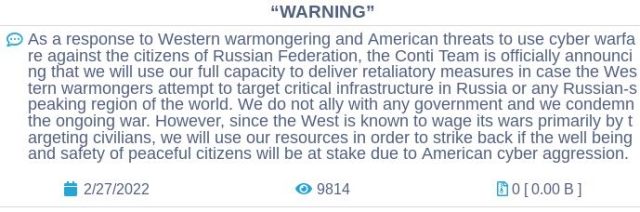
In a single different tweet, ContiLeaks wrote, “Glory for Ukraine!” This implied that the leak was once motivated, at the least in fragment, to answer a press release posted to Conti’s place on the darkish net that neighborhood members would “make use of our corpulent potential to convey retaliatory measures in case the Western Warmongers try to focal degree on critical infrastructure in Russia or any Russian-speaking station of the enviornment.”
KrebsOnSecurity, citing Alex Holden, the Ukrainian-born founding father of the Milwaukee-primarily based totally cyber intelligence agency Help Safety, has reported that the ContiLeaks is a Ukrainian safety researcher. “Right here is his design to conclude them in his ideas at the least,” KrebsOnSecurity provides. Fully completely different researchers beget speculated that the leaker is a Ukrainian worker or enterprise affiliate of Conti who broke with Conti’s Russia-primarily based totally leaders after they pledged enhance for the Kremlin.
In all, the leaks—which might nicely nicely be archived proper right here—story practically two years’ value of the neighborhood’s interior workings. On September 22, 2020, as an illustration, a Conti chief the utilization of the sort out Hof revealed that one thing perceived to be terribly unhealthy with Trickbot, a for-rent botnet that Conti and different crime teams outmoded to deploy their malware.
“The one who made this garbage did it completely,” Hof wrote whereas poring over a mysterious implant any particular person had place aside in to motive Trickbot-infected machines to disconnect from the assert and protect watch over server that fed them directions. “He knew how the bot works, i.e. he perchance noticed the availability code, or reversed it. Plus, he by some means encrypted the config, i.e. he had an encoder and a deepest key, plus uploaded all of it to the admin panel. It’s simply actual some extra or a lot much less sabotage.”
There will be dismay… and groveling
Seventeen days after Hof delivered the analysis, The Washington Publish reported that the sabotage was once the work of the US Cyber Painting, an arm of the Division of Protection headed by the director of the Nationwide Safety Company.
As Conti members tried to rebuild their malware infrastructure in unhurried October, its community of contaminated strategies mushroomed to include 428 medical suppliers and merchandise inside the US, KrebsOnSecurity reported. The management decided to make make use of of the substitute to reboot Conti’s operations by deploying its ransomware concurrently to neatly being care organizations that have been buckling below that pressure of a world pandemic.
“Fuck the clinics inside the usa this week,” a Conti supervisor with the sort out Goal wrote on October 26, 2020. “There will be dismay. 428 hospitals.”
Fully completely different chat logs analyzed by KrebsOnSecurity show Conti workers grumbling about low pay, lengthy hours, grueling work routines, and bureaucratic inefficiencies.
On March 1, 2021, as an illustration, a low-level Conti worker named Carter reported to superiors that the bitcoin fund outmoded to pay for VPN subscriptions, antivirus product licenses, up to date servers, and enviornment registrations was once instant by $1,240.
Eight months later, Carter was once as quickly as some other time groveling.
“Howdy, we’re out of bitcoins,” Carter wrote. “4 up to date servers, three vpn subscriptions, and 22 renewals are out. Two weeks forward of renewals for $960 in bitcoin 0.017. Please ship some bitcoins to this pockets, thanks.”

