
Getty Pictures
Hackers backed by North Korea’s govt exploited a extreme Chrome zero-day in an try and infect the pc strategies of an entire bunch of of us working in a large substitute of industries, together with the data media, IT, cryptocurrency, and financial providers and merchandise, Google said Thursday.
The flaw, tracked as CVE-2022-0609, become as quickly as exploited by two separate North Korean hacking teams. Each teams deployed the similar exploit tools on websites that each belonged to official organizations and had been hacked or had been dwelling up for the inform goal of serving assault code on unsuspecting visitors. One neighborhood become as quickly as dubbed Operation Dream Job, and it targeted greater than 250 of us working for 10 diversified corporations. The alternative neighborhood, recognized as AppleJeus, targeted 85 customers.
Dream jobs and cryptocurrency riches
“We suspect that these teams work for the similar entity with a shared current chain, therefore the train of the similar exploit tools, nonetheless each function with a inform mission dwelling and deploy diversified methods,” Adam Weidemann, a researcher on Google’s menace analysis neighborhood, wrote in a publish. “It is conceivable that different North Korean executive-backed attackers preserve entry to the similar exploit tools.”
Operation Dream Job has been lively since no not as much as June 2020, when researchers at safety company ClearSky seen the neighborhood focused on protection and governmental corporations. Obnoxious guys targeted explicit workers within the organizations with unfaithful affords of a “dream job” with corporations just like Boeing, McDonnell Douglas, and BAE. The hackers devised an advise social-engineering marketing campaign that outmoded fictitious LinkedIn profiles, emails, WhatsApp messages, and make contact with calls. The aim of the marketing campaign become as quickly as each to seize cash and settle for intelligence.
AppleJeus, in the meantime, dates abet to no not as much as 2018. That is when researchers from safety company Kaspersky observed North Korean hackers focused on a cryptocurrency trade the train of malware that posed as a cryptocurrency buying and promoting utility.
The AppleJeus operation become as quickly as principal for its train of a malicious app that become as quickly as written for macOS, which agency researchers said become as quickly as doubtlessly the primary time an APT—temporary for presidency-backed “advanced persistent menace neighborhood”—outmoded malware to specialise in that platform. Moreover mighty become as quickly because the neighborhood’s train of malware that ran totally in reminiscence with out writing a file to the onerous pressure, an advanced characteristic that makes detection mighty extra sturdy.
One in all the two teams (Weidemann did no longer assert which one) moreover outmoded a pair of of the similar rob an eye fixed on servers to infect safety researchers closing 12 months. The marketing campaign outmoded fictitious Twitter personas to manufacture relationships with the researchers. As quickly as a stage of believe become as quickly as established, the hackers outmoded each an Net Explorer zero-day or a malicious Visible Studio enterprise that purportedly contained supply code for a proof-of-belief exploit.
In February, Google researchers realized of a extreme vulnerability being exploited in Chrome. Agency engineers mounted the vulnerability and gave it the designation CVE-2022-0609. On Thursday, the agency outfitted extra predominant features in regards to the vulnerability and the way the two North Korean hackers exploited it.
Operation Dream Job despatched targets emails that alleged to advance from job recruiters working for Disney, Google, and Oracle. Hyperlinks embedded into the email correspondence spoofed official job searching websites just like Actually and ZipRecruiter. The websites contained an iframe that resulted within the exploit.
Right here is an occasion of 1 amongst the pages outmoded:
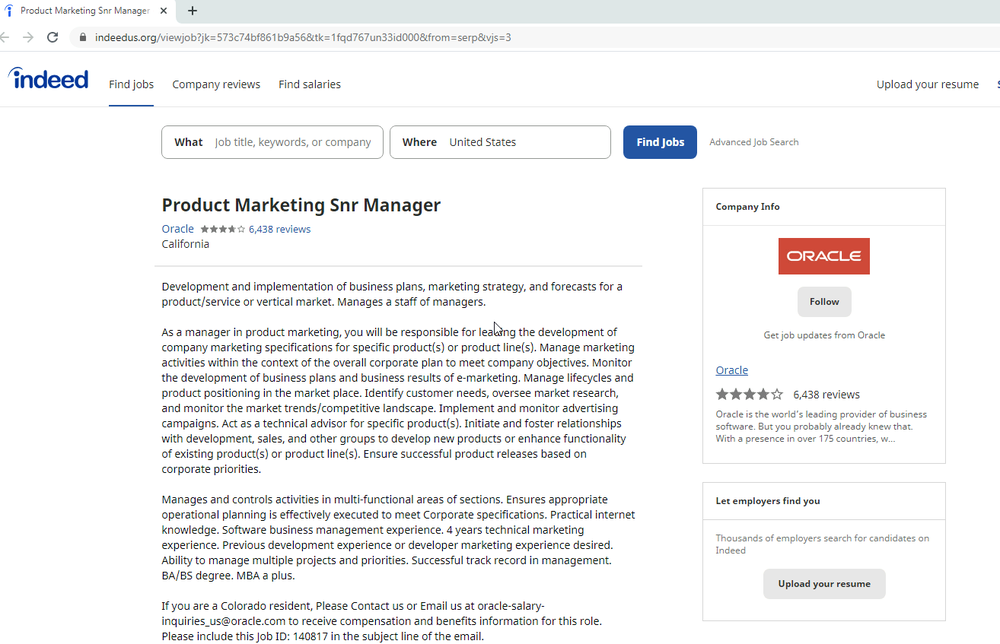
Members of Operation AppleJeus compromised the websites of no not as much as 2 official financial providers and merchandise corporations and a variety of advert hoc websites pushing malicious cryptocurrency apps. Luxuriate within the Dream Job websites, the websites outmoded by AppleJeus moreover contained iframes that resulted within the exploit.
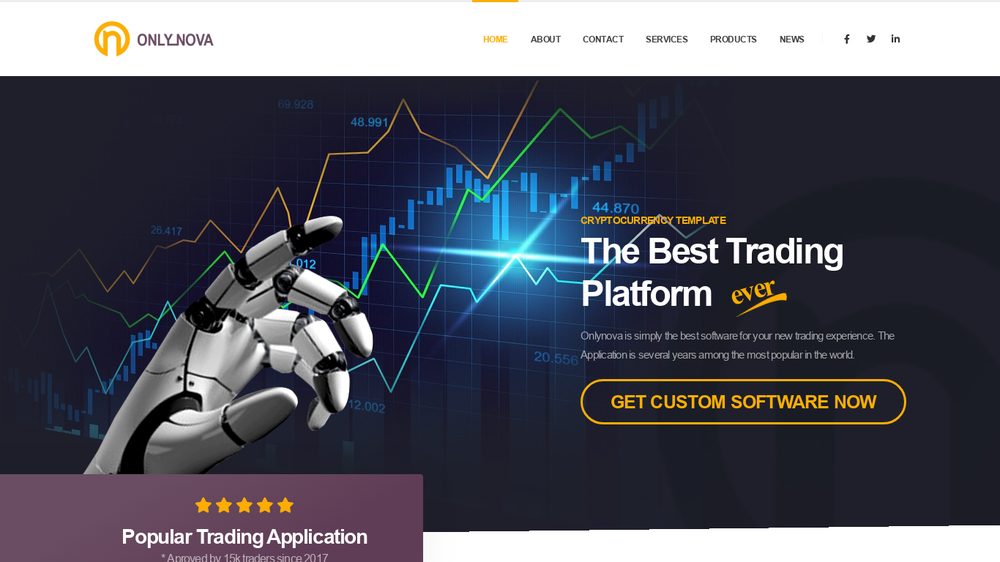
A unfaithful app pushed in Operation AppleJeus
Is there a sandbox obtain away on this tools?
The exploit tools become as quickly as written in a way to scrupulously cowl the assault by, amongst different issues, disguising the exploit code and triggering a methods off code execution very best in seize situations. The tools moreover seems to be like to take care of outmoded a separate exploit to interrupt out of the Chrome safety sandbox. The Google researchers had been unable to look out out that obtain away code, leaving provoke the likelihood that the vulnerability it exploited has however to be patched.

