ADDING CLOUT TO FAKE APPS —
Getting previous the App Retailer gatekeeper has at all times been difficult. Listed under are two contemporary packages.
Dan Goodin –

Scammers pushing iOS malware are stepping up their recreation by abusing two salubrious Apple features to avoid App Retailer vetting necessities and trick people into placing in malicious apps.
Apple has extended required that apps stroll a safety assessment and be admitted to the App Retailer ahead of they’re going to furthermore be put in on iPhones and iPads. The vetting prevents malicious apps from making their attain onto the gadgets, the place they are able to then recall cryptocurrency and passwords or create numerous infamous actions.
A put up printed Wednesday by safety company Sophos sheds light on two extra up to date suggestions being long-established in an organized crime marketing campaign dubbed CryptoRom, which pushes unfounded cryptocurrency apps to unsuspecting iOS and Android prospects. Whereas Android permits “sideloading” apps from third-social gathering markets, Apple requires iOS apps to return from the App Retailer, after they’ve handed by an intensive safety assessment.
Extra inexpensive and simpler
Enter TestFlight, a platform Apple makes available for the beta trying out of latest apps. By placing in Apple’s TestFlight app from the App Retailer, any iOS shopper can obtain and arrange apps that indulge in not however handed the vetting path of. As soon as TestFlight is put in, the patron can obtain the unvetted apps the utilization of hyperlinks attackers put up on rip-off websites or in emails. Of us can use TestFlight to ask as much as 10,000 testers the utilization of their electronic message deal with or by sharing a public hyperlink.
“A few of the victims who contacted us reported they’d been urged to arrange what seemed as if it might be BTCBOX, an app for a Jap cryptocurrency alternate,” Jagadeesh Chandraiah, a malware analyst at safety company Sophos wrote. “We additionally discovered unfounded websites that posed as a result of the cryptocurrency mining company BitFury peddling unfounded apps by TestFlight. We proceed to watch numerous CryptoRom apps the utilization of the identical attain.”
Wednesday’s put up confirmed a great deal of of the images long-established throughout the CryptoRom marketing campaign. iOS prospects who took the bait obtained a hyperlink that, when clicked, induced the TestFlight app to obtain and arrange the unfounded cryptocurrency app.

Sophos
Chandraiah acknowledged that the TestFlight vector provides attackers with benefits not available with greater-known App Retailer bypass ways that additionally abuse salubrious Apple features. One such attribute is Apple’s Massive Signature platform, which allows people to make the most of their Apple developer story to comment apps on a exiguous advert hoc basis. The completely different attribute is the corporate’s Developer Problem Program. It lets gigantic organizations deploy proprietary apps for internal use with out employees having to make the most of the App Retailer. Each suggestions require scammers to pay cash and particular numerous hurdles.
By distinction, Chandraiah acknowledged, TestFlight:
is more economical to make the most of than numerous schemes because of all you would like is an IPA file with a compiled app.The distribution is dealt with by any particular person else, and when (or if) the malware will get noticed and flagged, the malware developer can simply switch on to the subsequent provider and originate once more. [TestFlight] is most in vogue by malicious app builders in some situations over Massive Signature or Problem Signature as a result of it’s bit more economical and seems to be to be like additional salubrious when disbursed with the Apple Check Flight App. The assessment path of could possibly be believed to be much less stringent than App Retailer assessment.
That’s not all
The put up acknowledged the CryptoRom scammers are the utilization of a 2nd Apple attribute is conception as WebClips to additionally disguise their actions. That attribute—is conception as WebClips—provides a webpage hyperlink straight to an iPhone residence conceal throughout the type of an icon which will possibly properly possibly furthermore be puzzled with a benign app. WebClips seems to be after a shopper has saved a web-based hyperlink.
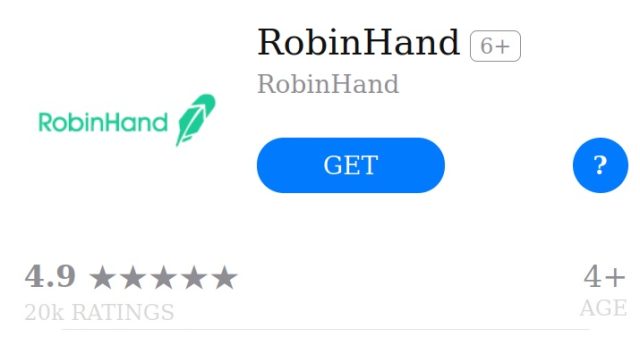
The Sophos researcher acknowledged CryptoRom can use WebClips in order so as to add clout to malicious URLs pushing unfounded apps. Proper right here’s an icon for an app often called RobinHand that’s designed to imitate the salubrious Robinhood buying and selling app.
Sophos
The CryptoRom scammers rely intently on social engineering. They use a differ of ruses to create a relationship with targets even though they by no functionality meet nose to nose. Social networks, relationship websites, and relationship capabilities are amongst such ruses. In numerous situations, the scammers begin relationships by “apparently random WhatsApp messages providing the recipients funding and buying and selling pointers.”
The abuse of TestFlight and WebClips is at chance of be noticed by savvy Internet prospects, nonetheless much less skilled people could possibly properly possibly simply salvage fooled. iOS prospects should serene stay cautious of anyplace of residing, electronic message, or message that instructs them to obtain apps from a supply numerous than the reputable App Retailer. An Apple consultant acknowledged this toughen net web page reveals the way you per probability can steer particular of and story scams. Apple has additional steerage right here and right here.

