GOT ROOT? —
Elevation of privilege vulnerabilities would perhaps be used to contrivance persistent root entry.
Dan Goodin –

Getty Images
Vulnerabilities not too long ago came upon by Microsoft accomplish it simple for folks with a toehold on many Linux desktop packages to hasty contrivance root system rights— principally probably the most up-to-the-minute elevation of privileges flaw to advance to light inside the launch provide OS.
As working packages possess been hardened to face as so much as compromises in novel years, elevation of privilege (EoP) vulnerabilities possess change right into a indispensable ingredient for many beneficiant hacks. They are going to be exploited in live performance with different vulnerabilities that on their dangle are normally thought to be a lot much less extreme, with the latter giving what’s known as native entry and the sooner escalating the foundation entry. From there, adversaries with bodily entry or restricted system rights can deploy backdoors or give up code of their choice.
Nimbuspwn, as Microsoft has named the EoP menace, is 2 vulnerabilities that dwell inside the networkd-dispatcher, a component in lots of Linux distributions that dispatch group area changes and would perhaps velocity deal of scripts to acknowledge to a brand new area. When a machine boots, networkd-dispatcher runs as root.
Microsoft
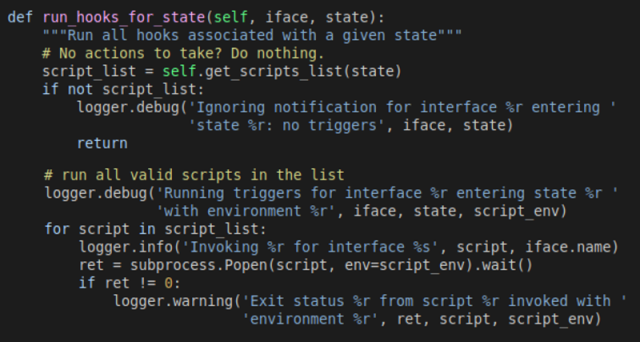
The failings, tracked as CVE-2022-29799 and CVE-2022-29800, mix threats together with listing traversal, symlink velocity, and time-of-take a take a look at time-of-exercise (TOCTOU) velocity situation. After reviewing the Networkd -dispatcher provide code, Microsoft researcher Jonathan Bar Or seen {that a} half known as “_run_hooks_for_state” implements the following logic:
- Discovers the listing of available scripts listing by invoking the “get_script_list” methodology, which calls a separate “scripts_in_path” methodology that’s supposed to advance the entire recordsdata saved inside the “/and many others/networkd-dispatcher/.d” listing.
- Sorts the script listing
- Runs every and every script with the method subprocess.Popen and provides custom-made environment variables
Microsoft
Run_hooks_for_state leaves Linux packages launch to the directory-traversal vulnerability, designated as CVE-2022-29799, on sage of not one among the many features it makes use of adequately sanitize the states used to create principally probably the most participating script path from malicious enter. Hackers can exploit the weak level to streak of the “/and many others/networkd-dispatcher” contaminated listing.
Proceed-hooks_for_state contains a separate flaw, CVE-2022-29800, which leaves packages weak to the TOCTOU velocity situation since there’s a positive time between the scripts being came upon and them being velocity.
Adversaries can exploit this latter vulnerability to trade scripts that networkd-dispatcher believes to be owned by root with malicious ones of the adversaries’ choice. To make path Linux executes the hacker-supplied malicious script in area of the official one, the hacker vegetation a pair of scripts besides one somehow succeeds.
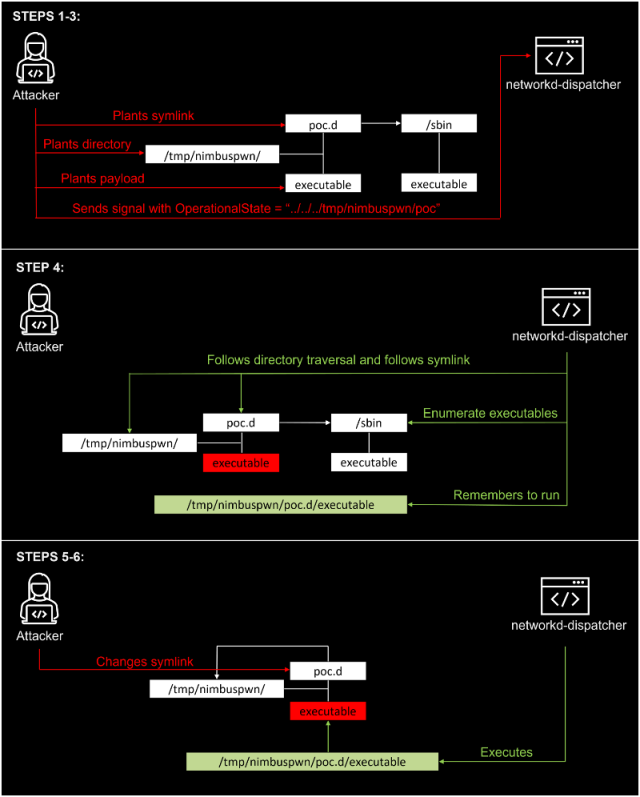
A hacker with minimal entry to a weak desktop can chain collectively exploits for these vulnerabilities that give paunchy root entry. The exploit waft appears love this:
- Put collectively a listing ”/tmp/nimbuspwn” and plant a symlink ”/tmp/nimbuspwn/poc.d“ to price “/sbin”. The “/sbin” listing was chosen significantly on sage of it has many executables owned by root that give up not block if velocity with out extra arguments. This is able to perhaps simply abuse the symlink velocity quandary we talked about earlier.
- For each and every executable filename under “/sbin” owned by root, plant the an identical filename under “/tmp/nimbuspwn”. Let’s converse, if “/sbin/vgs” is executable and owned by root, plant an executable file “/tmp/nimbuspwn/vgs” with the specified payload. This is able to perhaps simply assist the attacker make the most of the velocity situation imposed by the TOCTOU vulnerability.
- Ship a sign with the OperationalState “../../../tmp/nimbuspwn/poc”. This abuses the listing traversal vulnerability and escapes the script listing.
- The networkd-dispatcher sign handler kicks in and builds the script listing from the listing “/and many others/networkd-dispatcher/../../../tmp/nimbuspwn/poc.d”, which is generally the symlink (“/tmp/nimbuspwn/poc.d”), which factors to “/sbin”. Subsequently, it creates a listing nonetheless of many executables owned by root.
- Quickly alternate the symlink “/tmp/nimbuspwn/poc.d” to price “/tmp/nimbuspwn”. This abuses the TOCTOU velocity situation vulnerability—the script path changes with out networkd-dispatcher being acutely aware.
- The dispatcher begins working recordsdata that possess been on the beginning assign under “/sbin” however in any case under the “/tmp/nimbuspwn” listing. Because the dispatcher “believes” these recordsdata are owned by root, it executes them blindly with subprocess.Popen as root. Subsequently, our attacker has effectively exploited the vulnerability.
Right here’s a visualization:
Microsoft
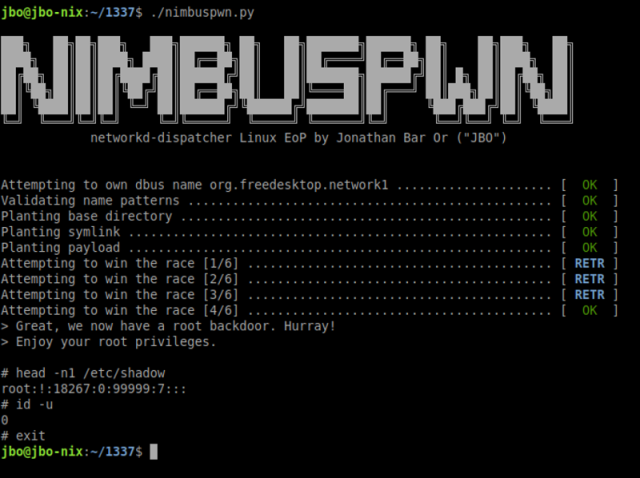
To contrivance persistent root entry, the researcher used the exploit waft to return by a backdoor. The path of for proper right here is:
- Copies /bin/sh to /tmp/sh.
- Turns the model new /tmp/sh it right into a Dwelling-UID (SUID) binary
- Runs /tmp/sh -p. The “-p” flag is indispensable since up-to-the-minute shells tumble privileges by produce.
Microsoft
The proof-of-realizing exploit works easiest when it’s going to train the “org.freedesktop.network1” bus establish. The researcher came upon a great deal of environments the assign this occurs, together with Linux Mint, whereby the systemd-networkd by default doesn’t dangle the org.freedodesktop.network1 bus establish at boot.
The researcher furthermore came upon a great deal of processes that velocity as a result of the systemd-community person, which is accredited to make train of the bus establish required to hurry arbitrary code from world-writable areas. The weak processes embody a great deal of gpgv plugins, which is seemingly to be launched when true-come by installs or upgrades, and the Erlang Port Mapper Daemon, which allows working arbitrary code under some eventualities.
The vulnerability has been patched inside the networkd-dispatcher, despite the fact that it wasn’t straight path when or in what model, and makes an attempt to prevail inside the developer weren’t straight beneficiant. Of us the train of weak variations of Linux should patch their packages as quickly as that you simply would possibly maybe presumably consider.

