ZUORAT —
Router-stalking ZuoRAT is seemingly the work of a complicated nation-reveal, researchers prepare.
Dan Goodin –

Getty Images
An unusually developed hacking staff has spent almost two years infecting a massive sequence of routers in North The US and Europe with malware that takes paunchy administration of related gadgets working Home windows, macOS, and Linux, researchers reported on Tuesday.
To this degree, researchers from Lumen Utilized sciences’ Murky Lotus Labs prepare they’ve recognized in any case 80 targets contaminated by the stealthy malware, infecting routers made by Cisco, Netgear, Asus, and DayTek. Dubbed ZuoRAT, the an extended way-off fetch admission to Trojan is share of a broader hacking promoting marketing campaign that has existed since in any case the fourth quarter of 2020 and continues to attribute.
A excessive stage of sophistication
The invention of personalized-constructed malware written for the MIPS construction and compiled for small place of work and residential place of work routers is critical, particularly given its differ of capabilities. Its capability to enumerate all gadgets related to an contaminated router and achieve the DNS lookups and community visitors they ship and obtain and dwell undetected is the hallmark of a extraordinarily refined danger actor.
“Whereas compromising SOHO routers as an fetch admission to vector to assemble fetch admission to to an adjoining LAN simply is not a unique methodology, it has seldom been reported,” Murky Lotus Labs researchers wrote. “Equally, experiences of specific person-in-the-heart vogue assaults, similar to DNS and HTTP hijacking, are even rarer and a mark of a flowery and centered operation. The devour of those two ways congruently demonstrated a excessive stage of sophistication by a danger actor, indicating that this promoting marketing campaign was once doubtless carried out by a reveal-sponsored group.”
The promoting marketing campaign comprises in any case 4 gadgets of malware, three of them written from scratch by the chance actor. Basically essentially the most vital half is the MIPS-basically primarily based ZuoRAT, which intently resembles the Mirai Information superhighway of Issues malware that completed chronicle-breaking disbursed denial-of-provider assaults that crippled some Information superhighway firms and merchandise for days. ZuoRAT usually will get place in by exploiting unpatched vulnerabilities in SOHO gadgets.
As soon as place in, ZuoRAT enumerates the gadgets related to the contaminated router. The danger actor can then devour DNS hijacking and HTTP hijacking to house off the related gadgets to arrange numerous malware. Two of these malware gadgets—dubbed CBeacon and GoBeacon—are personalized-made, with the primary written for Home windows in C++ and the latter written in Lunge for inferior-compiling on Linux and macOS gadgets. For flexibility, ZuoRAT might infect related gadgets with the broadly outdated Cobalt Strike hacking instrument.
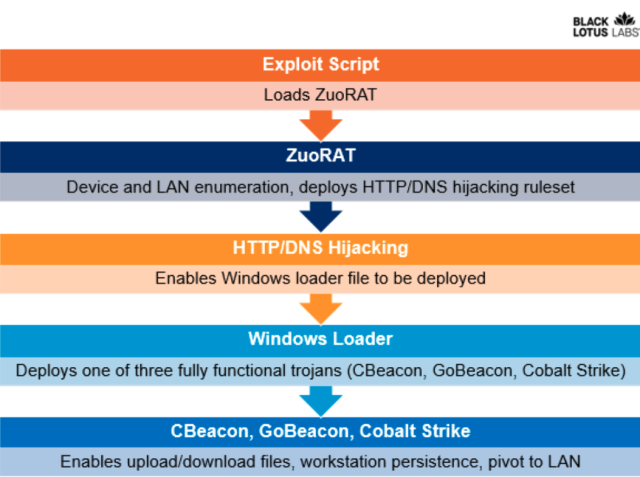
Murky Lotus Labs
ZuoRAT can pivot infections to related gadgets the devour of 1 in each of two options:
- DNS hijacking, which replaces the respectable IP addresses similar to a site similar to Google or Fb with a malicious one operated by the attacker.
- HTTP hijacking, during which the malware inserts itself into the connection to generate a 302 error that redirects the person to a decided IP deal with.
Deliberately complicated
Murky Lotus Labs acknowledged the reveal and administration infrastructure outdated throughout the promoting marketing campaign is intentionally complicated in an try to veil what’s happening. One house of infrastructure is outdated to control contaminated routers, and every other is reserved for the related gadgets in the event that they’re later contaminated.
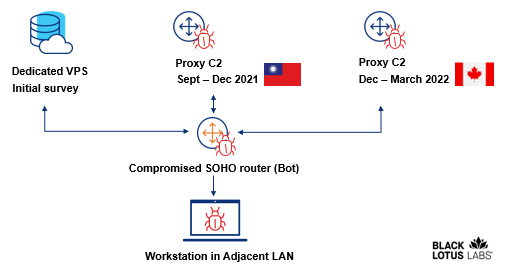
The researchers noticed routers from 23 IP addresses with a continual connection to a administration server that they think about was once performing an preliminary watch to look out out if the targets had been of pastime. A subset of these 23 routers later interacted with a Taiwan-basically primarily based proxy server for 3 months. A additional subset of routers circled to a Canada-basically primarily based proxy server to obfuscate the attacker’s infrastructure.
This graphic illustrates the steps listed alive to.
The danger actors additionally disguised the landing internet web page of a administration server to seem at love this:
Murky Lotus Labs
The researchers wrote:
Murky Lotus Labs visibility signifies ZuoRAT and the correlated task symbolize a extraordinarily centered promoting marketing campaign in opposition to US and Western European organizations that blends in with typical cyber internet visitors via obfuscated, multistage C2 infrastructure, seemingly aligned with a whole lot of phases of the malware an infection. The extent to which the actors resolve misery to hide the C2 infrastructure cannot be overstated. First, to handbook away from suspicion, they handed off the preliminary exploit from a devoted digital private server (VPS) that hosted benign lisp. Subsequent, they leveraged routers as proxy C2s that hid in simple leer via router-to-router communication to additional keep away from detection. And eventually, they circled proxy routers periodically to handbook away from detection.
The invention of this ongoing promoting marketing campaign is the righteous one affecting SOHO routers since VPNFilter, the router malware created and deployed by the Russian authorities that was once stumbled on in 2018. Routers are usually overpassed, particularly throughout the work-from-home technology. Whereas organizations usually relish strict requirements for what gadgets are allowed to hitch, few mandate patching or numerous safeguards for the gadgets’ routers.
Adore most router malware, ZuoRAT cannot live on a reboot. Merely restarting an contaminated instrument will resolve away the preliminary ZuoRAT exploit, consisting of information saved in a brief report. To completely improve, then as quickly as extra, contaminated gadgets have to be manufacturing facility reset. Sadly, throughout the event related gadgets had been contaminated with the varied malware, they might be capable of’t be disinfected so with out issues.

