THERE’S A HOLE IN THE BUCKET —
Leak of credentials may perchance properly properly perhaps be venerable in huge present-chain assaults.
Dan Goodin –

Getty Images
A service that helps open supply builders write and take a look at software is leaking hundreds of authentication tokens and varied security-sensitive secrets and techniques. Lots of these leaks enable hackers to uncover entry to the private accounts of builders on Github, Docker, AWS, and varied code repositories, safety consultants said in a model new report.
The supply of the third-birthday social gathering developer credentials from Travis CI has been an ongoing say since at the very least 2015. At the moment, safety vulnerability service HackerOne reported {that a} Github fable it venerable had been compromised when the service uncovered an uncover entry to token for undoubtedly considered one of many HackerOne builders. A an identical leak offered itself once more in 2019 and once more supreme yr.
The tokens give anyone with uncover entry to to them the pliability to learn or regulate the code saved in repositories that distribute an untold choice of ongoing software capabilities and code libraries. The flexibility to type unauthorized uncover entry to to such tasks opens the chance of current chain assaults, all of the technique through which risk actors tamper with malware previous to or not it is distributed to prospects. The attackers can leverage their capacity to tamper with the app to deal with huge numbers of tasks that depend on the app in manufacturing servers.
Regardless of this being a recognized safety say, the leaks be happy continued, researchers within the Nautilus group on the Aqua Safety agency are reporting. A sequence of two batches of recordsdata the researchers accessed the spend of the Travis CI programming interface yielded 4.28 million and 770 million logs from 2013 through May perchance properly presumably additionally 2022. After sampling a miniature share of the info, the researchers got here all of the technique through what they think about are 73,000 tokens, secrets and techniques, and reasonably a number of credentials.
“These uncover entry to keys and credentials are linked to widespread cloud service providers, along with GitHub, AWS, and Docker Hub,” Aqua Safety said. “Attackers can spend this delicate recordsdata to impress huge cyberattacks and to modify laterally within the cloud. Anyone who has ever venerable Travis CI is doubtlessly uncovered, so we advocate rotating your keys immediately.”
Travis CI is a supplier of an an growing variety of total put together is called staunch integration. Usually abbreviated as CI, it automates the technique of setting up and testing every and every code commerce that has been dedicated. For each and every commerce, the code is ceaselessly constructed, examined, and merged proper right into a shared repository. Given the diploma of uncover entry to CI desires to work successfully, the environments on the whole retailer uncover entry to tokens and varied secrets and techniques that current privileged uncover entry to to delicate facets inside the cloud fable.
The uncover entry to tokens got here all of the technique through by Aqua Safety enthusiastic personal accounts of a large fluctuate of repositories, along with Github, AWS, and Docker.

Aqua Safety
Examples of uncover entry to tokens that had been uncovered include:
- Entry tokens to GitHub that may enable privileged uncover entry to to code repositories
- AWS uncover entry to keys
- Units of credentials, every now and then an email correspondence or username and password, which permit uncover entry to to databases equal to MySQL and PostgreSQL
- Docker Hub passwords, which may moreover result in fable takeover if MFA (multi-say authentication) is not going to be any longer activated
The next graph reveals the breakdown:
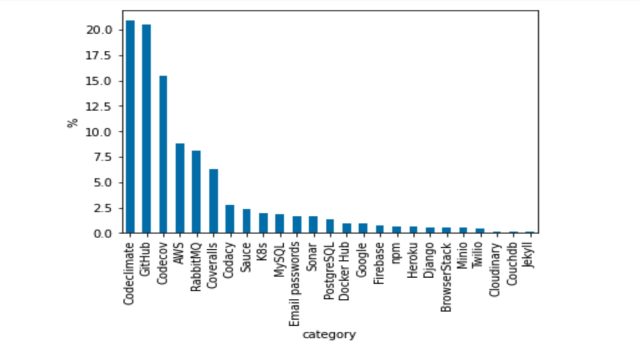
Aqua Safety
Aqua Safety researchers added:
We got here all of the technique through hundreds of GitHub OAuth tokens. It’s secure to determine that at the very least 10-20% of them are are residing. Particularly different people that had been present in current logs. We simulated in our cloud lab a lateral skedaddle state of affairs, which is based solely solely on this preliminary uncover entry to state of affairs:
1. Extraction of a GitHub OAuth token via uncovered Travis CI logs.
2. Discovery of delicate recordsdata (i.e., AWS uncover entry to keys) in personal code repositories the spend of the uncovered token.
3. Lateral skedaddle makes an attempt with the AWS uncover entry to keys in AWS S3 bucket service.
4. Cloud storage object discovery via bucket enumeration.
5. Data exfiltration from the purpose’s S3 to attacker’s S3.
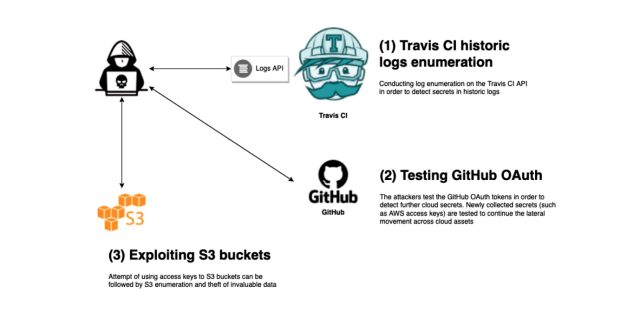
Aqua Safety
Travis CI representatives did in a roundabout technique reply to an email correspondence searching for situation for this put up. Given the routine nature of this publicity, builders ought to all the time proactively rotate uncover entry to tokens and varied credentials periodically. They need to all the time moreover ceaselessly scan their code artifacts to assemble clear they set aside not maintain credentials. Aqua Safety has additional recommendation in its put up.

