INDUSTRIAL CONTROL SYSTEMS —
A whole ecosystem of sketchy software is focused on doubtlessly main infrastructure.
Dan Goodin –
Getty Pictures
From the what-might probably well-presumably-bolt-spoiled data comes this: Folks hawking password-cracking software are targeted on the {hardware} outdated in industrial-alter services with malicious code that makes their applications section of a botnet, a researcher reported.
Misplaced passwords occur in lots of organizations. A programmable widespread sense controller—outdated to automate processes inner factories, electrical vegetation, and different industrial settings, lets ship, might be put up and largely forgotten over the following years. When a alternative engineer later identifies a trouble affecting the PLC, they’d effectively watch the now lengthy-long gone regular engineer by no means left the passcode within the relieve of prior to departing the corporate.
In accordance with a weblog submit from security agency Dragos, a whole ecosystem of malware makes an attempt to capitalize on cases fancy this one inner industrial services. On-line commercials fancy these under promote password crackers for PLCs and human-machine interfaces, which could probably effectively be the workhorses inner these environments.
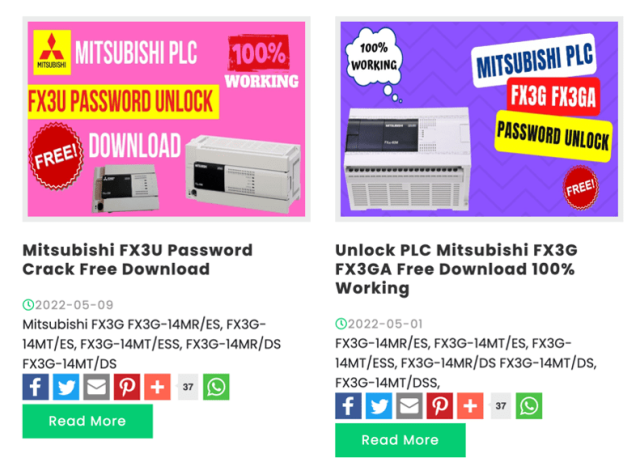
Dragos
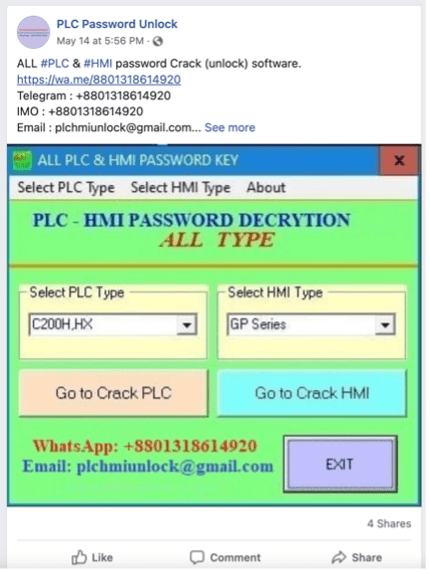
Dragos
When your industrial scheme is section of a botnet
Dragos—which helps firms exact industrial alter applications in opposition to ransomware, tell-sponsored hackers, and functionality saboteurs—not too prolonged beforehand carried out a routine vulnerability analysis and came upon software marketed as password cracker for the DirectLogic 06, a PLC supplied by Automation Allege. The software recovered the password, however not by the on a regular basis method to cracking the cryptographic hash. As an alternative, the software exploited a nil-day vulnerability in Computerized Allege PLCs that uncovered the passcode.
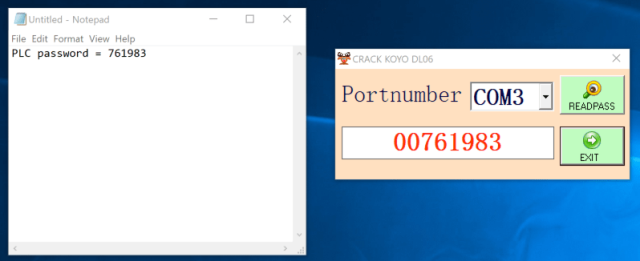
Dragos
“Outdated be taught targeted on DirectLogic PLCs has resulted in a success cracking recommendations,” Dragos researcher Sam Hanson wrote. “On the alternative hand, Dragos came upon that this exploit does not crack a scrambled mannequin of the password as traditionally thought of in commonplace exploitation frameworks. As an alternative, a specific byte sequence is disbursed by the malware dropper to a COM port.”

Dragos
The vulnerability, and a linked one moreover came upon by Hanson, occupy now been patched and are tracked as CVE-2022-2033 and CVE-2022-2004. The latter vulnerability can recuperate passwords and ship them to a a ways-off hacker, bringing the severity score to 7.5 out of a possible 10.
In addition to getting higher the password, the software Hanson analyzed moreover construct in malware recognized as Sality. It made the contaminated scheme section of a botnet and monitored the clipboard of the contaminated workstation each half of 2nd for any information linked to cryptocurrency pockets addresses.
“If thought of, the hijacker replaces the tackle with one owned by the likelihood actor,” Hanson acknowledged. “This in-proper-time hijacking is an environment friendly method to retract cryptocurrency from clients eager to switch funds and will increase our confidence that the adversary is financially motivated.”
Hanson went on to assert that he has came upon password crackers marketed on-line for a large sequence of enterprise software supplied by different firms. They encompass:
| Vendor and Asset | System Kind |
| Automation Allege DirectLogic 06 | PLC |
| Omron CP1H | PLC |
| Omron C200HX | PLC |
| Omron C200H | PLC |
| Omron CPM2* | PLC |
| Omron CPM1A | PLC |
| Omron CQM1H | PLC |
| Siemens S7-200 | PLC |
| Siemens S7-200 | Mission File (*.mwp) |
| Siemens LOGO! 0AB6 | PLC |
| ABB Codesys | Mission File (*.professional) |
| Delta Automation DVP, ES, EX, SS2, EC Sequence | PLC |
| Fuji Electrical POD UG | HMI |
| Fuji Electrical Hakko | HMI |
| Mitsubishi Electrical FX Sequence (3U and 3G) | PLC |
| Mitsubishi Electrical Q02 Sequence | PLC |
| Mitsubishi Electrical GT 1020 Sequence | HMI |
| Mitsubishi Electrical GOT F930 | HMI |
| Mitsubishi Electrical GOT F940 | HMI |
| Mitsubishi Electrical GOT 1055 | HMI |
| Official-Face GP Official-Face | HMI |
| Official-Face GP | Mission File (*.prw) |
| Vigor VB | PLC |
| Vigor VH | PLC |
| Weintek | HMI |
| Allen Bradley MicroLogix 1000 | PLC |
| Panasonic NAIS F P0 | PLC |
| Fatek FBe and FBs Sequence | PLC |
| IDEC Company HG2S-FF | HMI |
| LG K80S | PLC |
| LG K120S | PLC |
Dragos examined completely the malware targeted on the DirectLogic gadgets, however a rudimentary prognosis of just some samples indicated they moreover contained malware.
“On the entire, it seems there may be an ecosystem for this fashion of software,” Hanson acknowledged. “Fairly a great deal of websites and multiple social media accounts exist all touting their password ‘crackers.’”
The yarn is pertaining to on yarn of it illustrates the likelihood posed to many industrial alter settings. The criminals within the relieve of the malware Dragos analyzed had been after cash, however there’s no motive extra malicious hackers out to sabotage a dam, vitality plant, or similar facility couldn’t produce a similar intrusion with technique extra extreme penalties.

