SESSIONMANAGER —
SessionManager scours memory for passwords, does recon, and installs authentic devices.
Dan Goodin –

Getty Photographs
Researchers enjoyment of recognized stealthy authentic malware that menace actors enjoyment of been the usage of for the previous 15 months to backdoor Microsoft Commerce servers after they have been hacked.
Dubbed SessionManager, the malicious instrument poses as a sound module for Cyber net Info Corporations and merchandise (IIS), the earn server construct in by default on Commerce servers. Organizations usually deploy IIS modules to streamline explicit processes on their net infrastructure. Researchers from safety company Kaspersky enjoyment of recognized 34 servers belonging to 24 organizations which enjoyment of been contaminated with SessionManager since March 2021. As of earlier this month, Kaspersky talked about, 20 organizations remained contaminated.
Stealth, persistence, energy
Malicious IIS modules provide an most attention-grabbing components to deploy extraordinarily environment friendly, persistent, and stealthy backdoors. As soon as construct in, they will reply to significantly crafted HTTP requests despatched by the operator instructing the server to attain emails, add extra malicious safe entry to, or use the compromised servers for clandestine options. To the untrained enjoyment of in thoughts, the HTTP requests peek unremarkable, regardless of the undeniable fact that they provide the operator full management over the machine.
“Such malicious modules in complete inquire of seemingly reputable nevertheless significantly crafted HTTP requests from their operators, set off actions fixed with the operators’ hidden directions if any, then transparently cross the inquire of of to the server for it to be processed lovely esteem each different inquire of of,” Kaspersky researcher Pierre Delcher wrote. “As a consequence, such modules are not with out issues observed by weird monitoring practices: they do not principally start suspicious communications to exterior servers, web directions by HTTP requests to a server that’s significantly uncovered to such processes, and their information are usually positioned in overlooked areas that grasp heaps of different reputable information.”
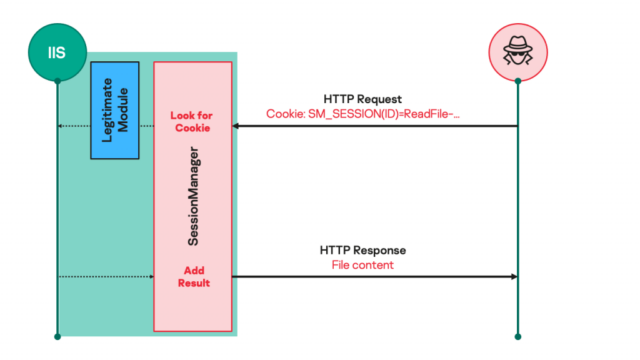
Kaspersky
As soon as SessionManager is deployed, operators use it to profile the contaminated ambiance extra, procure passwords saved in memory, and set up extra devices, along with a PowerSploit-essentially primarily based reflective loader, Mimikat SSP, ProcDump, and a sound Avast memory dump instrument. Kaspersky purchased a great deal of SessionManager variants that date discount to at the least March 2021. The samples put aside a legitimate evolution that has added extra features with each authentic model. Essentially the most current model of the malicious module comprises the subsequent:
Converse title
(SM_SESSION cookie imprint)Converse parameters
(extra cookies)Related capacity GETFILE FILEPATH: route of file to be examine. FILEPOS1: offset at which to open studying, from file open. FILEPOS2: most greater than a few of bytes to review.
Be taught the declare materials of a file on the compromised server and ship it to the operator as an HTTP binary file named frigid.rar. PUTFILE FILEPATH: route of file to be written. FILEPOS1: offset at which to open writing.
FILEPOS2: offset reference.
FILEMODE: requested file safe entry to kind.
Write arbitrary declare materials to a file on the compromised server. The info to be written within the required file is handed inside the HTTP inquire of of physique. DELETEFILE FILEPATH: route of file to be deleted. Delete a file on the compromised server. FILESIZE FILEPATH: route of file to be measured. Find the dimensions (in bytes) of the required file. CMD None. Pace an arbitrary course of on the compromised server. The method to shuffle and its arguments are specified by the HTTP inquire of of physique the usage of the format: t. The commonplace output and mistake information from course of execution are despatched discount as ghastly textual declare materials to the operator within the HTTP response physique. PING None. Check out for SessionManager deployment. The “Wokring OK” (sic.) message shall be despatched to the operator within the HTTP response physique. S5CONNECT S5HOST: hostname to attach with (outlandish with S5IP). S5PORT: offset at which to open writing.
S5IP: IP deal with to attach with if no hostname is given (outlandish with S5HOST).
S5TIMEOUT: most lengthen in seconds to allow for connection.
Be part of from compromised host to a specified community endpoint, the usage of a created TCP socket. The integer identifier of the created and linked socket shall be returned as a result of the imprint of the S5ID cookie variable within the HTTP response, and the spot of the connection shall be reported within the HTTP response physique. S5WRITE S5ID: identifier of the socket to jot right down to, as returned by S5CONNECT. Write information to the required linked socket. The info to be written within the required socket is handed inside the HTTP inquire of of physique. S5READ S5ID: identifier of the socket to review from, as returned by S5CONNECT. Be taught information from the required linked socket. The examine information is distributed discount inside the HTTP response physique. S5CLOSE S5ID: identifier of the socket to close, as returned by S5CONNECT. Discontinuance an current socket connection. The spot of the operation is returned as a message inside the HTTP response physique.
Be acutely aware ProxyLogon?
SessionManager will get construct in after menace actors enjoyment of exploited vulnerabilities recognized as ProxyLogon inside Microsoft Commerce servers. Kaspersky has found it infecting NGOs, governments, militaries, and industrial organizations in Africa, South The USA, Asia, and Europe.
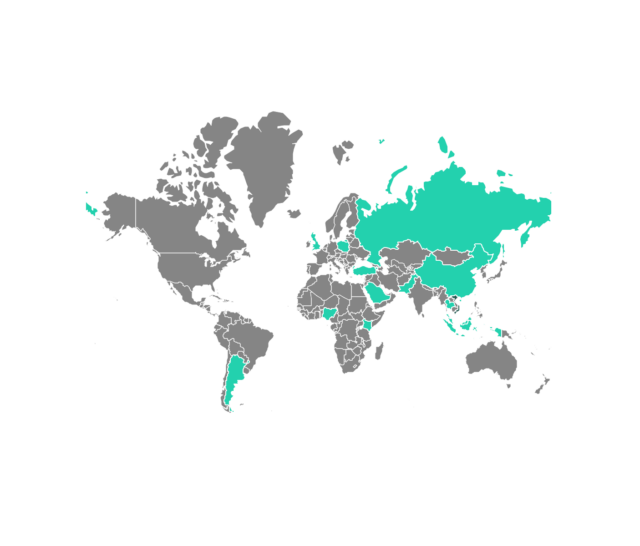
Kaspersky
Kaspersky talked about it has medium-to-excessive self belief {that a} beforehand recognized menace actor that researchers title Gelsemium has been deploying SessionManager. Safety company ESET printed a deep dive on the neighborhood (PDF) closing 300 and sixty 5 days. Kaspersky’s attribution is fixed with the overlap of code feeble by the two teams and victims centered.
Disinfecting servers which enjoyment of been hit by SessionManager or an equivalent malicious IIS modules is a elaborate course of. Kaspersky’s publish comprises indicators that organizations can use to look out out in the event that they’ve been contaminated and steps they could furthermore serene plan shut within the occasion they’ve been contaminated.

