LIGHTNING FRAMEWORK —
This modular malware framework for Linux has lengthy gone undocumented until now.
Dan Goodin –

The instrument framework has flip into wanted to rising merely about all difficult instrument on the second. The Django Net framework, for instance, bundles the overall libraries, characterize information, and different substances obligatory to like a flash type and deploy internet apps, making it a mainstay at firms fancy Google, Spotify, and Pinterest. Frameworks present a platform that performs whole capabilities fancy logging and authentication shared all the perfect map through an app ecosystem.
Closing week, researchers from safety agency Intezer printed the Lightning Framework, a modular malware framework for Linux that has lengthy gone undocumented until now. Lightning Framework is post-exploit malware, that means it will get put in after an attacker has already received uncover entry to to a centered machine. As quickly as put in, it would almost certainly presumably present a pair of of the an equivalent efficiencies and stride to Linux compromises that Django offers for internet development.
“It is unusual to leer such an intricate framework developed for concentrating on Linux methods,” Ryan Robinson, a safety researcher at Intezer, wrote in a publish. “Lightning is a modular framework we discovered that has a plethora of capabilities, and the flexibility to put in a couple of types of rootkit, besides to the aptitude to certain plugins.”
Intezer
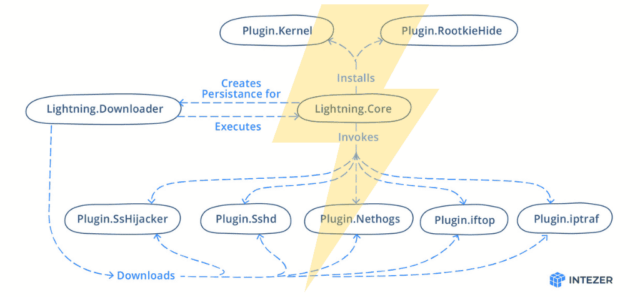
Lightning consists of a downloader named Lightning.Downloader and a core module named Lightning.Core. They hook up with a particular relate and encourage a watch on server to obtain instrument and glean directions, respectively. Prospects can then certain any of not decrease than seven modules that increase out all types of different corrupt points. Capabilities consist of each passive and energetic communications with the danger actor, along with opening an actual shell on the contaminated machine and a polymorphic malleable relate.
The framework has every passive and energetic capabilities for verbal change with the danger actor, along with opening up SSH on an contaminated machine, and improve for connecting to narrate and encourage a watch on servers that make use of malleable profiles. Malware frameworks have existed for years, nonetheless there aren’t many who present so mighty complete improve for the hacking of Linux machines.
In an electronic message, Robinson stated Intezer discovered the malware on VirusTotal. He wrote:
The entity that submitted it seems to be associated to a Chinese language language manufacturing organisation that makes tiny motor residence tools. We discovered this per different submissions from the an equivalent submitter. I fingerprinted the server that we used to title the corporate and so they had been actually the utilization of Centos (which the malware modified into as soon as compiled for). However this serene is not stable sufficient to enact that they’d been the targets or contaminated with the malware. We’ve bought not found the comfort present given that e-newsletter. The legitimate factor which we hope to look out is without doubt one of the encrypted malleable C2 configuration profiles. It may possibly presumably give us community IOCs to have an effect on pivoting off.
Intezer modified into as soon as able to have an effect on components of the framework nonetheless not each little factor. From the information the corporate researchers had been prepared to investigate, they might properly perhaps infer the presence of different modules. The corporate outfitted the next overview:
| Title | Title on Disk | Description |
| Lightning.Downloader | kbioset | The facility module that downloads the core module and its plugins |
| Lightning.Core | kkdmflush | The indispensable module of the Lightning Framework |
| Linux.Plugin.Lightning.SsHijacker | soss | There is a reference to this module nonetheless no pattern discovered inside the wild but. |
| Linux.Plugin.Lightning.Sshd | sshod | OpenSSH with hardcoded inner most and host keys |
| Linux.Plugin.Lightning.Nethogs | nethoogs | There is a reference to this module nonetheless no pattern discovered inside the wild but. Presumably the instrument Nethogs |
| Linux.Plugin.Lightning.iftop | iftoop | There is a reference to this module nonetheless no pattern discovered inside the wild but. Presumably the instrument iftop |
| Linux.Plugin.Lightning.iptraf | iptraof | There is a reference to this module nonetheless no pattern discovered inside the wild but. Presumably the instrument IPTraf |
| Linux.Plugin.RootkieHide | libsystemd.so.2 | There is a reference to this module nonetheless no pattern discovered inside the wild but. LD_PRELOAD Rootkit |
| Linux.Plugin.Kernel | elastisearch.ko | There is a reference to this module nonetheless no pattern discovered inside the wild but. LKM Rootkit |
Thus far there do not look like any acknowledged circumstances of the Lightning Framework being actively utilized inside the wild. Nonetheless, given the abundance of readily available capabilities, deliver-of-the-artwork stealth is undoubtedly section of the tools.

