GOT MFA? —
Promoting and advertising marketing campaign that steals piece of email has targeted on the least 10,000 organizations since September.
Dan Goodin –

Getty Footage
On Tuesday, Microsoft detailed an ongoing effective-scale phishing advertising marketing campaign that may hijack particular person accounts after they’re protected with multi-factor authentication measures designed to pause such takeovers. The menace actors slack the operation, who personal targeted 10,000 organizations since September, personal worn their covert win entry to to sufferer piece of email accounts to trick staff into sending the hackers cash.
Multi-factor authentication—now and again known as two-factor authentication, MFA, or 2FA—is the gold long-established for legend security. It requires the legend particular person to show their id within the assemble of 1 factor they personal or assign watch over (a bodily security key, a fingerprint, or face or retina scan) along with one factor they know (their password). Because the rising narrate of MFA has stymied legend-takeover campaigns, attackers personal came upon methods to strike encourage.
The adversary within the coronary heart
Microsoft seen a advertising marketing campaign that inserted an attacker-controlled proxy diagram between the legend customers and the work server they tried to log into. When the person entered a password into the proxy diagram, the proxy diagram despatched it to the correct server after which relayed the correct server’s response encourage to the person. As soon as the authentication turned into as soon as carried out, the menace actor stole the session cookie the legit diagram despatched, so the person would not personal to be reauthenticated at each distinctive web page visited. The promoting marketing campaign started with a phishing piece of email with an HTML attachment ensuing within the proxy server.
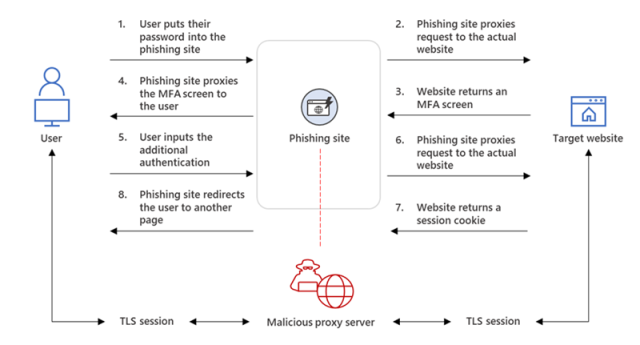
Get dangle of bigger / The phishing net diagram intercepting the authentication course of.
“From our remark, after a compromised legend signed into the phishing diagram for the primary time, the attacker worn the stolen session cookie to authenticate to Outlook on-line (outlook.diagram of economic.com),” members of the Microsoft 365 Defender Evaluation Staff and the Microsoft Menace Intelligence Center wrote in a weblog publish. “In a great deal of circumstances, the cookies had an MFA declare, which contrivance that though the group had an MFA coverage, the attacker worn the session cookie to achieve win entry to on behalf of the compromised legend.”
Throughout the days following the cookie theft, the menace actors accessed worker piece of email accounts and appeared for messages to relate in commerce piece of email compromise scams, which tricked targets into wiring efficient sums of cash to accounts they believed belonged to co-workers or commerce companions. The attackers worn these piece of email threads and the hacked worker’s strong id to influence the various event to hold out a price.
To assign the hacked worker from discovering the compromise, the menace actors created inbox options that robotically moved specific emails to an archive folder and marked them as be taught. Over the following few days, the menace actor logged in periodically to confirm for brand new emails.
“On one event, the attacker carried out a great deal of fraud makes an attempt concurrently from the an identical compromised mailbox,” the weblog authors wrote. “Every time the attacker came upon a model distinctive fraud goal, they up so a good distance the Inbox rule they created to include these distinctive targets’ group domains.”
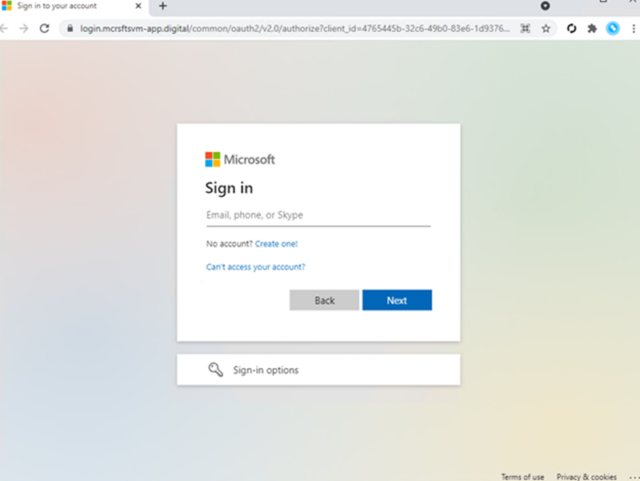
Get dangle of bigger / Pattern phishing landing web page.
Microsoft
Nothing in Microsoft’s legend should be taken to assert that deploying MFA is simply not any longer one amongst top-of-the-line measures to pause legend takeovers. That mentioned, now not all MFA is equal. One-time authentication codes, even when despatched by SMS, are a good distance higher than nothing, nevertheless they proceed to be phishable or interceptable by means of extra unique abuses of the SS7 protocol worn to ship textual content messages.
One of many crucial efficient kinds of MFA readily accessible are these that are compliant with necessities area by the industry-huge FIDO Alliance. All these MFA narrate a bodily security key that may contrivance as a dongle from companies treasure Yubico or Feitian and even an Android or iOS instrument. The authentication may presumably additionally contrivance from a fingerprint or retina scan, neither of which ever mosey away the conclude-individual instrument to pause the biometrics from being stolen. What all FIDO-properly matched MFA has in conventional is that it is a good distance going to’t be phished and makes use of encourage-conclude packages immune to this assemble of ongoing advertising marketing campaign.

