FROM RUSSIA WITH …. —
Hacks additionally exploit crucial Follina vulnerability and phishing campaigns.
Dan Goodin –

Getty Pictures
Professional-Russian risk actors are persevering with their unrelenting pursuit of Ukrainian targets, with an array of campaigns that embrace unfaithful Android apps, hack assaults exploiting crucial vulnerabilities, and email correspondence phishing assaults which might be trying and harvest login credentials, researchers from Google acknowledged.
One in every of the extra modern campaigns got here from Turla, a Russian-talking salubrious persistent risk actor that has been vigorous since in spite of everything 1997 and is among the many most technically refined on this planet. In keeping with Google, the crew centered pro-Ukrainian volunteers with Android apps that posed as launchpads for performing denial-of-provider assaults in opposition to Russian web sites.
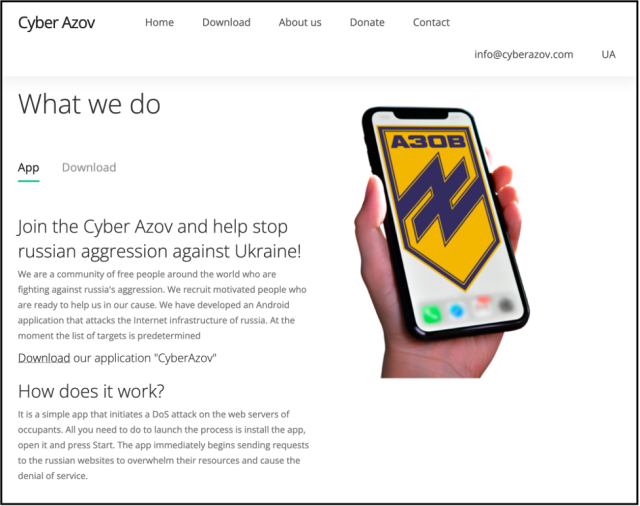
“All you receive to assemble to starting out the machine is set up the app, originate it and press starting,” the unfaithful internet place selling the app claimed. “The app directly begins sending requests to the Russian web sites to crush their assets and set off the denial of supplier.”
The truth is, a researcher with Google’s risk prognosis crew acknowledged, the app sends a single GET request to a goal internet place. Sluggish the scenes, a totally totally different Google researcher knowledgeable Vice that the app was designed to plan out the person’s Internet infrastructure and “work out the place the contributors which could maybe maybe presumably very properly be doubtlessly doing these sorts of assaults are.”
The apps, hosted on a web-based internet web page spoofing the Ukrainian Azov Regiment, mimicked yet another Android app Google first noticed in March that additionally claimed to assemble DoS assaults in opposition to Russian web sites. Not identical to the Turla apps, stopwar.apk, because the latter app was named, despatched a steady circulation of requests except the person stopped them.
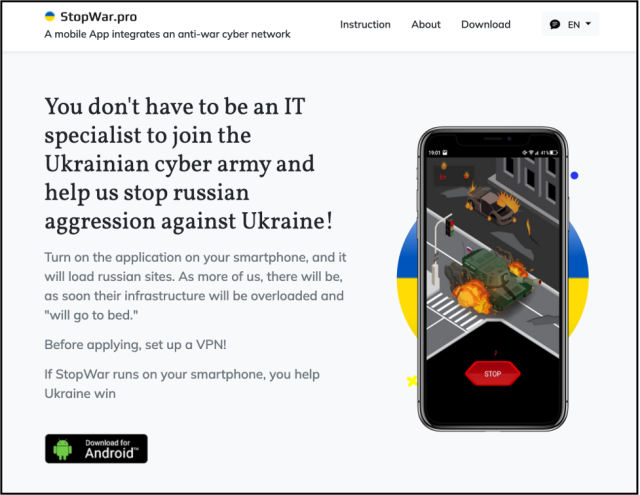
“In keeping with our prognosis, we think about that the StopWar app was developed by pro-Ukrainian builders and was the inspiration for what Turla actors primarily primarily primarily based their unfaithful CyberAzov DoS app off of,” Google researcher Billy Leonard wrote.
Different hacking teams backed by the Kremlin receive additionally centered Ukrainian teams. Campaigns included the exploitation of Follina, the title given to a crucial vulnerability in all supported variations of Home windows that was actively centered within the wild for bigger than two months as a 0-day.
Google researchers confirmed a CERT-UA narrative from June that acknowledged a totally totally different Kremlin-subsidized hacking crew—tracked beneath a vogue of names together with Esteem Preserve, is known as Pawn Storm, Sofacy Neighborhood, and APT28—was additionally exploiting Follina in an try and infect targets with malware is known as CredoMap. Moreover, Google acknowledged that Sandworm—however one other crew backed by the Russian govt—was additionally exploiting Follina. That marketing campaign previous compromised govt accounts to ship hyperlinks to Microsoft Workplace paperwork hosted on compromised domains, primarily specializing in media organizations in Ukraine.
CERT-UA
Safety agency Palo Alto Networks, within the interval in-between, reported on Tuesday that Russia’s Cloaked Usa hacking crew (also called APT29, Nobelium, and Cozy Preserve) had additionally stepped up malware assaults for the reason that starting of Russia’s invasion of Ukraine, in part by making malicious recordsdata for obtain available on Dropbox and Google Energy. US and UK intelligence companies and merchandise receive publicly attributed APT29 to Russia’s International Intelligence Supplier (SVR).
“This aligns with the crew’s historical specializing in degree of curiosity, relationship assist to malware campaigns in opposition to Chechnya and different previous Soviet bloc international locations in 2008,” Palo Alto Networks researchers Mike Harbison and Peter Renals wrote. Extra recently, APT29 has been linked to a hack of the US Democratic Nationwide Committee say in 2016 and the SolarWinds provide-chain assaults from 2020.
Now not the entire risk teams specializing in Ukraine are Kremlin-subsidized, Google acknowledged. Now not too way back, a financially motivated actor tracked as UAC-0098 impersonated the Instruct Tax Supplier of Ukraine and delivered malicious paperwork that attempted to revenue from Follina. Google acknowledged the actor is a previous preliminary ransomware entry dealer that beforehand labored with the Conti ransomware crew.
On Wednesday, the US Cyber Narrate shared technical most well-known elements related to what the company acknowledged are fairly a little bit of sorts of malware specializing in Ukrainian entities in modern months. The malware samples are available on VirusTotal, Pastebin, and GitHub. Safety agency Mandiant acknowledged two separate espionage teams previous the malware, one tracked as UNC1151 and attributed by Mandiant to the Belarusian govt and the other tracked as UNC2589, which the agency acknowledged is “believed to behave in beef up of Russian govt interest and has been conducting intensive espionage assortment in Ukraine.”
The European Union also called out the Russian govt this week, noting {that a} latest distributed denial-of-provider marketing campaign was final essentially the most up-to-the-minute instance of cyberattacks it launched since its invasion.
“Russia’s unprovoked and unjustified army aggression in opposition to Ukraine has been accompanied by a most well-known develop of malicious cyber actions, together with by a inserting and concerning collection of hackers and hacker teams indiscriminately specializing in most well-known entities globally,” EU officers wrote. “This develop in malicious cyber actions, within the context of the battle in opposition to Ukraine, creates unacceptable risks of spillover results, misinterpretation, and certain escalation.”

