VPN safety —
VPNs on Apple cellular devices reportedly protect connections beginning and advise data.
Kevin Purdy –

Getty Images
A safety researcher says that Apple’s iOS devices kind now not completely route all community visitors through VPNs as a client may perchance effectively additionally put a matter to, a in all probability safety convey the instrument maker has recognized about for years.
Michael Horowitz, a longtime laptop safety blogger and researcher, places it plainly—if contentiously—in a repeatedly up thus far weblog put up. “VPNs on iOS are damaged,” he says.
Any third-occasion VPN seems to work inside the beginning up, giving the instrument a novel IP take care of, DNS servers, and a tunnel for distinctive visitors, Horowitz writes. Nonetheless durations and connections established ahead of a VPN is activated enact now not discontinuance and, in Horowitz’s findings with advanced router logging, can serene ship data outside the VPN tunnel whereas it is lively.
In different phrases, which it is important moreover put a matter to a VPN shopper to kill present connections ahead of establishing a legitimate connection in order that they’re normally re-established for the size of the tunnel. Nonetheless iOS VPNs can not appear to enact this, Horowitz says, a discovering that’s backed up by a similar doc from Can also simply 2020.
“Particulars leaves the iOS instrument outside of the VPN tunnel,” Horowitz writes. “Right here is now not a basic/legacy DNS leak, it is a ways a data leak. I confirmed this the utilization of a number of types of VPN and gear from a number of VPN suppliers. The most recent model of iOS that I examined with is 15.6.”
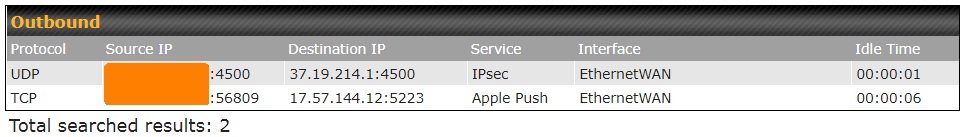
Security blogger Michael Horowitz’s logs veil a VPN-connected iPad reaching out to every his VPN supplier (37.19.214.1) and Apple Push (17.57.144.12). The Apple connection is outside the VPN and must doubtlessly advise his IP take care of if considered by an ISP or different occasions.
Privateness agency Proton beforehand reported an iOS VPN bypass vulnerability that started on the very least in iOS 13.3.1. Esteem Horowitz’s put up, ProtonVPN’s weblog famed {that a} VPN usually closes all present connections and reopens them inside a VPN tunnel, nonetheless that did not occur on iOS. Most present connections will inside the waste discontinue up for the size of the tunnel, nonetheless some, worship Apple’s push notification service, can closing for hours.
The precept convey with non-tunneled connections persisting is that they will be unencrypted and that the IP take care of of the customer and what they’re connecting to can be considered by ISPs and different occasions. “These at highest menace on yarn of of this safety flaw are of us in nations the set surveillance and civil rights abuses are customary,” ProtonVPN wrote on the time. That might perchance effectively additionally simply now not be a urgent matter for frequent VPN customers, nonetheless it is important.
ProtonVPN confirmed that the VPN bypass persevered in three subsequent updates to iOS 13. ProtonVPN indicated in its weblog put up that Apple would add efficiency to dam present connections, nonetheless this efficiency as added did now not appear to fabricate a distinction in Horowitz’s outcomes.
Horowitz examined ProtonVPN’s app in mid-2022 on an iPad iOS 15.4.1 and located that it serene allowed continuous, non-tunneled connections to Apple’s push service. The Smash Swap aim added to ProtonVPN, which describes its aim as blocking all community visitors if the VPN tunnel is misplaced, did now not cease leaks, primarily primarily based completely on Horowitz.
Horowitz examined all as quickly as extra on iOS 15.5 with a assorted VPN supplier and iOS app (OVPN, operating the WireGuard protocol). His iPad persevered to fabricate requests to every Apple providers and merchandise and to Amazon Net Providers and merchandise.
ProtonVPN had urged a workaround that grew to become as quickly as “almost as environment friendly” as manually closing all connections when beginning a VPN: Hook up with a VPN server, flip on airplane mode, then flip it off. “Your different connections must furthermore reconnect for the size of the VPN tunnel, although we is now not going to ensure this 100%,” ProtonVPN wrote. Horowitz means that iOS’s Airplane Mode features are so complicated as to fabricate this a non-answer.
We now savor reached out to every Apple and OpenVPN for commentary and must interchange this text with any responses.
Horowitz’s put up does now not supply specifics on how iOS may perchance effectively additionally restore the convey. He furthermore does now not take care of VPNs that supply “cut up tunneling,” focusing instead on the promise of a VPN taking photos all community visitors. For his phase, Horowitz recommends a $130 devoted VPN router as a with out a doubt legitimate VPN resolution.
VPNs, particularly industrial decisions, proceed to be an progressed share of Particulars superhighway safety and privateness. Selecting a “best VPN” has prolonged been a subject. VPNs can be introduced down by vulnerabilities, unencrypted servers, grasping data brokers, or by being owned by Fb.
(Replace 2: 58 pm ET: Up to date to deal with concept of cut up tunneling and VPN expectations.)

