SHARPTONGUE —
SHARPEXT has slurped up hundreds of emails within the earlier twelve months and retains bettering.
Dan Goodin –

Getty Pictures
Researchers have religion unearthed by no technique-earlier than-seen malware that hackers from North Korea had been utilizing to surreptitiously study and obtain e-mail and attachments from contaminated prospects’ Gmail and AOL accounts.
The malware, dubbed SHARPEXT by researchers from safety agency Volexity, makes use of suave approach to arrange a browser extension for the Chrome and Edge browsers, Volexity reported in a weblog submit. The extension cannot be detected by the e-mail providers and merchandise, and because the browser has already been authenticated utilizing any multifactor authentication protections in dwelling, this an rising variety of stylish safety measure performs no function in reining within the yarn compromise.
The malware has been in use for “successfully over a twelve months,” Volexity acknowledged, and is the work of a hacking crew the company tracks as SharpTongue. The crew is sponsored by North Korea’s authorities and overlaps with a crew tracked as Kimsuky by different researchers. SHARPEXT is targeted on organizations within the US, Europe, and South Korea that work on nuclear weapons and different factors North Korea deems well-known to its nationwide safety.
Volexity President Steven Adair acknowledged in an e-mail that the extension will get put in “by way of spear phishing and social engineering the put the sufferer is fooled into opening a malicious file. Beforehand we have now religion now seen DPRK menace actors launch spear phishing assaults the put your whole objective was to earn the sufferer to arrange a browser extension vs it being a submit exploitation mechanism for persistence and recordsdata theft.” In its contemporary incarnation, the malware works most effective on Residence home windows, however Adair acknowledged there is not any motive it could not be broadened to contaminate browsers engaged on macOS or Linux, too.
The weblog submit added: “Volexity’s soak up visibility exhibits the extension has been considerably suited, as logs purchased by Volexity outline the attacker was in a neighborhood to effectively take hundreds of emails from additional than one victims by way of the malware’s deployment.”
Putting in a browser extension all of the tactic by way of a phishing operation with out the rupture-person noticing simply is not straightforward. SHARPEXT builders have religion clearly paid consideration to examine love what’s printed right here, right here, and right here, which exhibits how a safety mechanism within the Chromium browser engine prevents malware from making adjustments to delicate individual settings. Each time a sound commerce is made, the browser takes a cryptographic hash of one of many code. At startup, the browser verifies the hashes, and if any of them do not match, the browser requests the conventional settings be restored.
For attackers to work spherical this security, they must first extract the next from the pc they’re compromising:
- A duplicate of the property.pak file from the browser (which contains the HMAC seed aged by Chrome)
- The individual’s S-ID value
- The same old Preferences and Rep Preferences information from the individual’s system
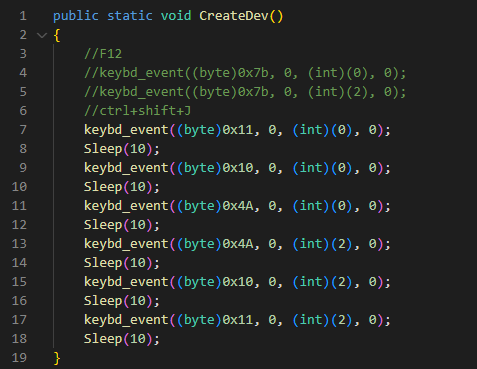
After modifying the necessity information, SHARPEXT robotically a whole bunch the extension and executes a PowerShell script that allows DevTools, a environment that allows the browser to bustle personalised code and settings.
“The script runs in an huge loop checking for processes related to the targeted browsers,” Volexity outlined. “If any targeted browsers are found working, the script checks the title of the tab for a specific key phrase (as an illustration, ‘05101190,’ or ‘Tab+’ looking on the SHARPEXT model). The express key phrase is inserted into the title by the malicious extension when an fascinating tab adjustments or when a web page is loaded.”
Volexity
The submit continued:
The keystrokes despatched are corresponding to
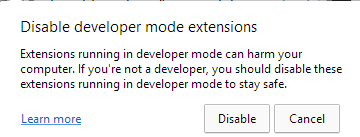
Protect watch over+Shift+J, the shortcut to allow the DevTools panel. Lastly, the PowerShell script hides the newly opened DevTools window by utilizing the ShowWindow() API and theSW_HIDEflag. On the rupture of this route of, DevTools is enabled on the fascinating tab, however the window is hidden.As successfully as, this script is aged to masks any dwelling home windows that can alert the sufferer. Microsoft Edge, as an illustration, periodically shows a warning message to the individual (Determine 5) if extensions are working in developer mode. The script repeatedly checks if this window seems and hides it by utilizing the
ShowWindow()and theSW_HIDEflag.
Volexity
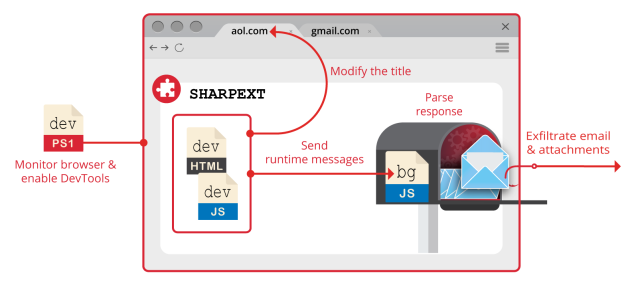
As quickly as put in, the extension can invent the next requests:
| HTTP POST Information | Description |
| mode=guidelines | Guidelines beforehand clear e-mail from the sufferer to substantiate that duplicates are now not uploaded. This guidelines is continually up to this point as SHARPEXT executes. |
| mode=area | Guidelines e-mail domains with which the sufferer has beforehand communicated. This guidelines is continually up to this point as SHARPEXT executes. |
| mode=dusky | Salvage a blacklist of e-mail senders that must be now not illustrious when accumulating e-mail from the sufferer. |
| mode=newD&d=[data] | Add a website to the guidelines of all domains seen by the sufferer. |
| mode=connect&identify=[data]&idx=[data]&physique=[data] | Add a peculiar attachment to the faraway server. |
| mode=uncommon&mid=[data]&mbody=[data] | Add Gmail information to the faraway server. |
| mode=attlist | Commented by the attacker; derive an attachments guidelines to be exfiltrated. |
| mode=new_aol&mid=[data]&mbody=[data] | Add AOL information to the faraway server. |
SHARPEXT permits the hackers to invent lists of e-mail addresses to brush apart and to retain video show of e-mail or attachments which have religion already been stolen.
Volexity created the next abstract of the orchestration of the numerous SHARPEXT components it analyzed:
Volexity
The weblog submit gives pictures, file names, and different indicators that skilled different folks can use to resolve within the occasion that they have been targeted or contaminated by this malware. The company warned that the menace it poses has grown over time and is doubtlessly to not go away any time quickly.
“When Volexity first encountered SHARPEXT, it perceived to be a software in early building containing an enormous quantity of bugs, a designate the software was immature,” the company acknowledged. “Basically essentially the most modern updates and ongoing repairs outline the attacker is attaining its targets, discovering value in persevering with to refine it.”

