DOING AN END-RUN ON EDRS —
Two of mainly probably the most large types of evasion are surprisingly large in opposition to EDRs.
Dan Goodin –

Getty Photographs / Aurich Lawson
Final yr, organizations spent $2 billion on merchandise that provide Endpoint Detection and Response, a considerably new fabricate of safety security for detecting and blocking malware concentrating on network-connected models. EDRs, as they’re repeatedly referred to as, signify a extra recent map to malware detection. Static prognosis, considered one of two extra damaged-down concepts, searches for suspicious indicators throughout the DNA of a file itself. Dynamic prognosis, the opposite extra established process, runs untrusted code inside a secured “sandbox” to analyze what it does to substantiate or now not it’s ranking before permitting it to glean fats system entry.
EDRs—which might be forecasted to generate earnings of $18 billion by 2031 and are bought by dozens of safety corporations—seize a wholly fairly just a few process. In assert of analyze the construction or execution of the code before time, EDRs computer screen the code’s habits because it runs inside a machine or community. In principle, it’ll shut down a ransomware assault in growth by detecting {that a} path of completed on tons of of machines throughout the earlier quarter-hour is encrypting recordsdata en masse. Not like static and dynamic analyses, EDR is resembling a safety guard that makes expend of machine studying to retain tabs in actual time on the actions inside a machine or community.
Nohl and Gimenez
Streamlining EDR evasion
Whatever the enjoyable surrounding EDRs, new be taught means that the safety they offer is now not all that arduous for expert malware builders to bypass. In truth, the researchers throughout the assist of the be taught estimate EDR evasion provides most large one additional week of development time to the traditional an an infection of a edifying organizational community. That’s as a result of two barely total bypass ways, specifically when blended, seem to work on most EDRs obtainable throughout the enterprise.
“EDR evasion is well-documented, nonetheless extra as a craft than a science,” Karsten Nohl, chief scientist at Berlin-based principally principally SRLabs, wrote in an e-mail. “What’s new is the perception that combining a number of well-recognized ways yields malware that evades all EDRs that we examined. This allows the hacker to streamline their EDR evasion efforts.”
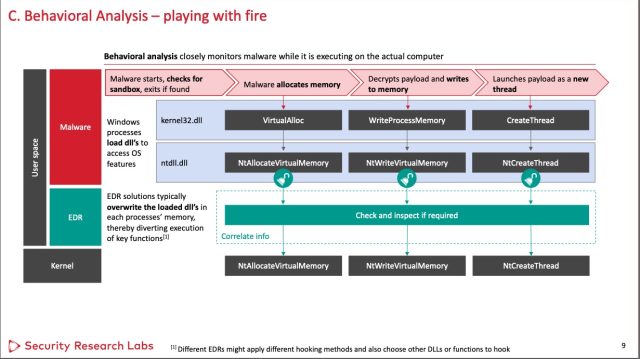
Each malicious and benign apps expend code libraries to work alongside with the OS kernel. To withhold out this, the libraries develop a reputation staunch away to the kernel. EDRs work by interrupting this normal execution drift. Instead of calling the kernel, the library first calls the EDR, which then collects knowledge about this map and its habits. To interrupt this execution drift, EDRs partly overwrite the libraries with additional code acknowledged as “hooks.”
Nohl and fellow SRLabs researcher Jorge Gimenez examined three extensively former EDRs bought by Symantec, SentinelOne, and Microsoft, a sampling they believe about barely represents the alternatives out there throughout the market as an entire. To the researchers’ shock, they got here throughout that each specific particular person three had been bypassed by using one or every and every of two barely uncomplicated evasion ways.
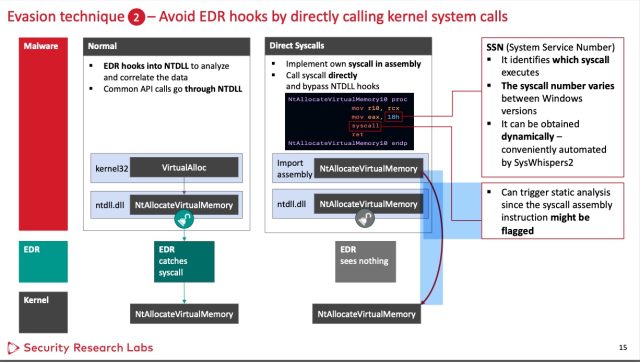
The ways seize scheme on the hooks the EDRs expend. The predominant process goes throughout the hook attribute and as an alternate makes order kernel system calls. Whereas a hit in opposition to all three EDRs examined, this hook avoidance has the ability to exasperate the suspicion of some EDRs, so or now not it’s now not foolproof.
Nohl and Gimenez
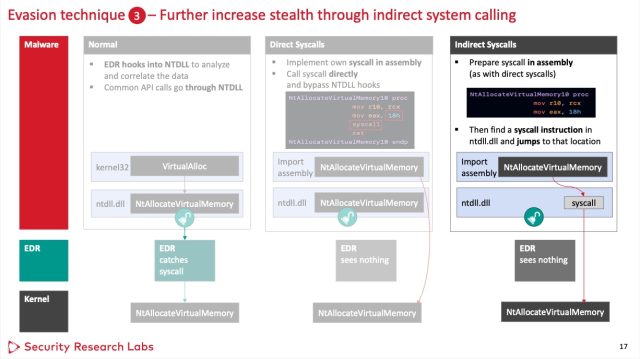
The second system, when applied in a dynamic hyperlink library file, additionally labored in opposition to all three EDRs. It entails utilizing most large fragments of the zigzag capabilities to retain from triggering the hooks. To withhold out this, the malware makes oblique system calls. (A Third system spirited unhooking capabilities labored in opposition to at least one EDR nonetheless was too suspicious to idiot the opposite two check out topic issues.)
Nohl and Gimenez
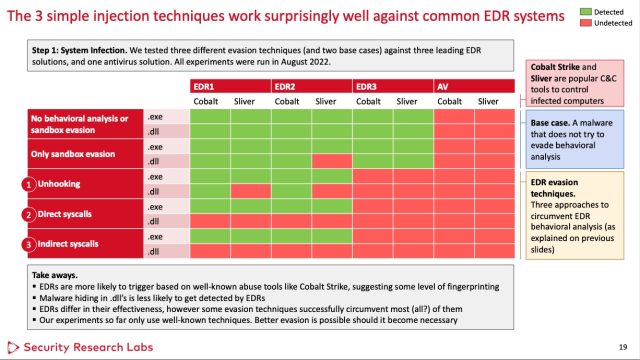
In a lab, the researchers packed two repeatedly former gadgets of malware—one referred to as Cobalt Strike and the opposite Silver—inside every and every an .exe and .dll file utilizing every and every bypass system. Among the EDRS—the researchers do not look like figuring out which one—did not detect any of the samples. The substitute two EDRs did not detect samples that got here from the .dll file after they former both system. For supreme measure, the researchers additionally examined a normal antivirus resolution.
Nohl and Gimenez
The researchers estimated that the traditional baseline time required for the malware compromise of a predominant firm or organizational community is ready eight weeks by a group of 4 consultants. Whereas EDR evasion is believed to slack the system, the revelation that two considerably uncomplicated ways can reliably bypass this security process that the malware builders would perhaps now not require mighty additional work as some would perhaps agree with.
“Complete, EDRs are including about 12 p.c or one week of hacking effort when compromising a edifying company—judged from the traditional execution time of a purple group whisper,” Nohl wrote.
The researchers provided their findings last week on the Hack throughout the Field safety conference in Singapore. Nohl talked about EDR makers should level of curiosity on detecting malicious habits extra generically barely than triggering most large on express habits of the preferred hacking devices, rather a lot like Cobalt Strike. This overfocus on express habits makes EDR evasion “too simple for hackers utilizing extra bespoke tooling,” Nohl wrote.
“Complementary to higher EDRs on endpoints, we restful be taught likely in dynamic prognosis inside sandboxes,” he added. “These can flee throughout the cloud or linked to e-mail gateways or internet proxies and filter malware before it even reaches the endpoint.”

